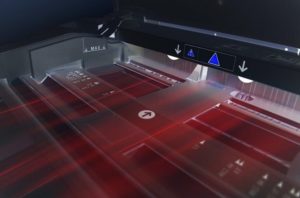
Printing devices are often overlooked when it comes to security. The reality is, cybercriminals can hack your printer to get confidential information.
Your printer is probably the last piece of computer equipment you thought needed protection from cybercriminals.
But the truth is very different.
Hackers actively try to locate the weakest links in security to gain access to and exploit valuable data. Among the weakest links are printers.
The thing with printers nowadays is that they have access to your devices, network, and the internet. This new open-access functionality makes them an ideal target for cyberattacks.
Unfortunately, many business owners overlook the importance of securing their printers and mainly focus on computers and mobile phones.
Most people still perceive printers as internal devices that serve basic functions. For this very reason, they are an easy target for cybercriminals.
Other than performing unauthorized print jobs, hackers can access confidential information as well as connected computers and networks all through a printer.
You may also not be aware of the amount of valuable data your printer can store about you – tax files, bank details, financial records, employee information, personal information, etc. All a hacker needs to do is get into the operating system of your printer, and they can collect this sensitive data.
If you’ve just realized the importance of securing your printer, keep reading. This article shares eight tips to help you do just that.
The 8 Tips
Tip #1: Make Sure Your Printers are Configured Correctly
Many things can make a printer vulnerable to cyber threats and security breaches. So, you want to get the basics right to ensure the attacks don’t happen to you.
To start, make sure to change the default password on your printer. Since anyone can access a printer remotely, a simple “123456” code won’t suffice.
Second, make sure you’re using your own router to print files remotely. Never connect to “Guest” networks.
Tip #2: Inspect Print Trays Regularly
This one is a no-brainer, but everyone could use it as a reminder. Make sure to check your print trays and get rid of unused pages carrying sensitive information. There’s no easier way to prevent data leaks than this.
Alternatively, you can get a shredder for your office and shred the papers you don’t want anyone to see.
Tip #3: Install Malware and Firmware Updates
Invest time and effort to ensure that your malware and firmware protection are up to date and can handle all types of hacks.
The good news is that many printers come with pre-built malware protection.
HP, for example, installs the HP “SureStart” software in their printers that monitors approaching targets when the printer is on. The software can shut down the device if an attack comes its way. This is a great way to prevent attacks from spreading further within the network.
Tip #4: Limit Access to the Network
Unprotected printers in a network are an extremely easy target for cybercriminals. Sure, businesses and offices require printers to access networks to perform remote prints but if you can do the job by disabling the network access, make sure you do that.
If not, tweak the printer and network settings to only allow the device to take print jobs from the network you trust. This will help avoid outside interference and security breaches.
Tip #5: Update Your Printers
Updating a printer is equally as important as updating your phone to the latest software. Much in the way iOS developers look for bugs and fix them in a new update, printer manufacturers work toward known device vulnerabilities and update the software for added protection.
Look for printer updates so you can easily overcome known threats to the printer. Ideally, update your printers every quarter to get the most out of the security benefits.
Tip #6: Install a Firewall
If you run an office, chances are you already have a firewall. But in case you missed this requirement, now’s the time to do it.
Using a reliable firewall helps keep printers safe from cybercriminals.
Your computers most likely come with pre-built firewalls, and all you need to do is keep them enabled. But there are also specialized firewalls for homes and offices that offer advanced security and make it virtually impossible for anyone to break in.
Tip #7: Encrypt Your Storage
Printers with shared networks can perform distance printing. When a print job is in transit and travels from a computer to a printer, hackers can intercept the data and exploit it.
To keep this from happening, encrypt your print jobs. Also, make sure the sensitive data on your printer’s hard or internal drive is encrypted as well.
Keep in mind that when you print a document, that file is often stored as an image within the printer and makes it an easy target for hackers. It’s why you should use an encryption tool to protect your data. Luckily, many modern printers have this tool pre-built.
You can use the tool to set up a secure password that allows printer storage encryption, remove user IDs and ex-employee access, delete documents from the print queue once they’re printed, and much more.
Tip #8: Educate Your Employees
If you work in an office, chances are you aren’t the only person using the printer. Everyone that has access to it needs to be aware of the responsibilities that come with its usage. Make sure to talk to your employees about ways to ensure both the physical and virtual safety of the printers.
Your staff should also be careful when using their mobile devices to print, as smartphones are easier to hack. Explain to them what phishing scams are and how they can avoid being the victim.
Finally, make sure it’s clear to them how they can use confidential information in your company.
It’s Time to Ensure Printer Security
Printers are the most overlooked devices when it comes to security. Given how most business owners consider them as merely internal devices whose sole function is to print documents, it’s no wonder they are a weak spot security-wise.
Whether you use printers in your office or at home, take a moment to see how you can enhance its security before your next printing job.
As cybercriminals are a growing concern, each of us is responsible for protecting our data. Luckily, the tips from this article will help you bring your printer’s security to another level.
Article used with permission from The Technology Press.
Read More

Getting used to Windows 11 shouldn’t be too challenging. On the contrary, the OS comes with several intuitive features to enhance productivity.
Microsoft recently introduced Windows 11 as the company’s latest operating system and compared to Windows 10, this OS has various features that can increase your productivity and provide a better user experience.
As soon as you start using Windows 11, you’ll notices the efficiency it brings to your work environment.
For example, it has refined several household features, such as video conferencing and video management. You also get enhanced note-taking, data input, and a user-friendly interface that should help you complete your duties more efficiently.
Many other features can help boost your productivity, and this article will talk about them in detail. We’ll also look at some features Microsoft didn’t include in the new version.
Windows 11 – What’s New?
Feature #1: New Taskbar
Previous Windows versions feature an iconic taskbar, but it can sometimes get clunky. Windows 11 provides a streamlined solution.
The new taskbar is perfect for expediting work, as it can contain a list of recent cloud and local files. You can also pin various apps to improve access and utilize a search bar that allows for convenient web browsing.
Another highlight of the taskbar is clean lines and widgets that display essential information (e.g., weather, photos, and news).
This should be a tremendous upgrade from the busy display of Windows 10.
Feature #2: Windows Grouping and Snapping
The enhanced Snap Group and Snap Layout features allow you to resize and manage windows more easily. You also get to keep essential apps grouped to maintain high productivity.
Using the feature is relatively straightforward: Just hover the mouse over the maximize button on the desired app to reveal your layout options. You can choose between several arrangements, such as four-app grids and side-by-side layouts.
And if your team needs to perform basic window management, they can still grab and pull windows to the edge of their screen.
This feature improves desktop organization, which is especially useful for people working with two or more monitors. They can reduce clutter rapidly, enabling them to focus on their tasks.
Feature #3: Improve Accessibility Options
Windows 11 follows in the footsteps of many smartphones to simplify setting changes and make them easily accessible. Pulling up your control panel now only requires one tap or click in the taskbar coroner, replicating Apple’s Control Centre.
Furthermore, Windows 11 apps feature aesthetic, curved corners, and your Settings incorporate more options you can tweak. For instance, blind or vision impaired users can take advantage of cutting-edge audio cues. There are also desktop themes to help reduce eye strain, which is essential if you work long hours.
On top of that, the new operating system has revamped voice typing. You can activate this with a simple keyboard shortcut. This feature supports most major languages, including English, German, Italian, French, Spanish, Simplified Chinese, and Portuguese.
Windows 11’s better accessibility means your team will no longer have to keep relying on your IT service provider to set things up for them.
Feature #4: Better App Store
Many apps can enhance workplace productivity, but you’ll first need to find them on your PC’s app store. Fortunately, Windows 11 came up with an organized and coherent platform to make the search easier.
Besides universal apps, you can check out the applications compatible with your devices. The platform can also handle programs from third-party stores and manage app installation on the internet.
Feature #5: Smooth Notetaking
If you’re using a touchscreen device, taking notes in Windows 11 should now be highly satisfying. This feature offers haptic feedback to generate physical sensations when drawing lines on the screen or checking boxes with your pen.
Moreover, the Ink Workspace allows you to add preferred apps instead of using the standard snipping tool and Whiteboard. It gives you easy access to creativity tools the moment you pull out your pen.
Which Features Were Left Behind?
Overall, Windows 11 should work great for your business but bear in mind that Microsoft left out some features that were a staple in previous versions:
Excluded Feature #1: Taskbar Customization
Windows 10 users can move their taskbar from the horizontal position to the left, right, or upper part of their screen. In contrast, the Windows 11 taskbar is fixed at the bottom of the display, and you can’t customize the dimensions.
The taskbar customization feature would have been helpful because it would let you use space more efficiently.
Another significant change is that you can no longer move the Time and Date on your taskbar. Windows 10 didn’t have this problem since you could toggle off the Clock feature in your Settings.
The default taskbar layout might be fine, but some users prefer higher customizability than what Windows 11 offers.
Excluded Feature #2: Drag-and-Drop Features
Windows 10 and some earlier versions allowed you to drag several items to change their position. For example, you could drag a Word document onto your Word icon on the taskbar to open it.
This function is disabled in Windows 11. There’s no way to drag and drop or save any program or file onto your taskbar.
Excluded Feature #3: Cortana
Cortana is a voice assistant counterpart of Siri, Alexa, and Google Assistant. Many people are used to it and may be disappointed to hear that it’s not a part of the Windows 11 system setup. You can’t even locate it in your start menu.
The good news is that the Cortana application can still be found – it’s just hidden away. You can enable it by visiting Settings and navigating to Apps & Features.
A Wise Investment
While Windows 11 isn’t perfect since it removed many valuable features, it’s still an excellent platform to help increase your productivity.
Whether you need to organize your desktop more conveniently or take enjoyable notes, the OS won’t let you down. Plus, you get a revamped taskbar and powerful Voice Typing compatible with most major languages.
Overall, Windows 11 can be a terrific asset for your business. Contact Databranch today at 716-373-4467 x 15 or [email protected] if you’re thinking about making the switch and would like to discuss options.
Article used with permission from The Technology Press.
Read More

Your data is pivotal to running a successful company. If you don’t have proper security measures in place, hackers can easily steal your data and take you out of business.
Cybercriminals might be the biggest threat facing your company. Besides gaining access to your money and accounts, they can also take over critical software, preventing you from collaborating with clients.
Any organization can fall victim to hacking. However, small and medium businesses are particularly at risk.
Why?
Too often, their owners don’t always address cybersecurity when launching their company. Sometimes, they even just hire the first IT service provider they see. They also don’t know how to shield themselves from online attackers, making them low-risk targets.
As a result, these organizations often go under due to the loss of sensitive data. It isn’t a risk you can take.
To help mitigate it, this article will introduce you to the various types of hackers and explain how to protect your business from them.
THE 5 TYPES OF HACKERS TO WATCH OUT FOR
1. Hackers Who are After Your Personal Information
Many hackers are dying to get their hands on the personal information of your clients and employees. It includes birth dates, financial data, and social security numbers.
Social security numbers might be the most valuable asset they want to get ahold of since cybercriminals can use them for various purposes. For instance, they can perform tax fraud, open credit accounts, and make other significant identity breaches.
In addition, financial data can be utilized for fraudulent activities and purchases, especially if it lacks robust digital security systems.
2. Hackers Who Want to get into the Digital Infrastructure
Storage and data servers are expensive – and hackers know that.
In order for them to cut costs, hackers may aim to store their applications and data on your infrastructure instead. The better your infrastructure, the more likely cybercriminals are to target it. This can strain your network to the limits and have devastating effects on your business.
Unsurprisingly, tech companies are some of the most common victims of this type of hacking.
The common indicators that a hacker has tapped into your digital infrastructure include:
- Running out of storage faster than usual
- Your network suffers slowdowns
- You may have unknown devices on your network.
3. Hackers Who are After Confidential Information
Few business aspects are as important as your intellectual property (IP). Your products and services enable you to stand out from the competition and strike a chord with the target audience.
A huge problem arises if hackers steal the design of your upcoming product before you launch it or submit your patent. A competitor may obtain the information, allowing them to hit the market first and undercut your sales.
4. Hackers Who Want to get Account Data
Sure, you and your IT service provider might have done enough so that hackers might not be able to obtain financial data. But are your employees’ accounts secure?
If hackers compromise them, they may let them run scams and gain information to disrupt your operations.
For example, losing CEO login credentials can be devastating. Besides granting hackers access to sensitive information, it also helps them impersonate the CEO. In return, they can solicit information from employees or clients and halt your operations.
This data breach can lead to widespread confusion, tarnishing your reputation.
5. Hackers Who Aim to Have Network Control
In some cases, hackers aren’t after data. Instead, they want to gain control of the entire network. And to make it happen, they launch ransomware attacks.
These activities enable them to lock you out of the system and make data inaccessible until you pay a ransom. They’re typically initiated through spam, phishing emails, and online ads.
The average ransom amount stands at approximately $30,000, but the loss caused by business disruption is much more significant.
HOW TO PROTECT YOUR BUSINESS
1. Investing in Security Resources
A key factor ignored by many owners is the amount of money and time devoted to cybersecurity. Avoid this mistake by allocating enough resources to set up solid defensive measures. Make sure to invest in a reliable IT service provider to help you out.
This way, your online accounts, hardware, and network should be more secure.
2. Training Your Team
Most security systems have weaknesses and their employees are usually the biggest ones.
For this reason, HR managers and CEOs should ensure their staff follows optimal security measures, both in-office and at home. They must all remember that any phone or laptop they use for work can be a weak point and entryway for hackers.
To introduce your employees to the best security practices, consider arranging security education and training for a month once a year. You can talk about different aspects of your company and the steps necessary to deter cybercriminals, for example.
Sound education can go a long way in promoting a healthy security culture.
Click here to learn more about Databranch’s Security Awareness Training Program!
3. Adding Authentication
There are many valuable tools you can use to fend off hackers. One of them is two-factor authentication (2FA) – a simple yet effective weapon against scammers.
This measure requires each user to verify their identity to access your system. You could use it on all business-related accounts
Furthermore, encourage your team members to activate 2FA on personal accounts. This way, they’ll be more likely to follow appropriate security practices, reducing the risk of compromised devices and data breaches.
4. Leveraging Software
Computer viruses are another go-to tool for hackers. And a great way to deal with them is to incorporate antivirus software.
Make sure your built-in antivirus software is up to date. Also, you can consider a corporate package from trusted companies like Webroot.
Each machine that can access work resources should rely on this software. Plus, the user should conduct weekly antivirus scans to lessen the chances of computers getting infected by a virus.
5. Performing Security Checks
Checking your system is vital for optimal cybersecurity. Solid antivirus software is practical, but you shouldn’t disregard manual scans. It’s crucial that your IT service provider does this periodically.
More specifically, check who’s accessed your network and make sure each point of access is authorized. Any suspicious activity must be reviewed and rooted out. Otherwise, these red flags can prove fatal for the company.
STAY ON THE SAFE SIDE
Battling hackers may not be the most exciting part of running a business. However, neglecting cybersecurity turns your company into a sitting duck for scammers. You may lose money, data, and your reputation might suffer irreparable damage.
While there isn’t a bulletproof solution, adopting the outlined tactics should be a strong starting point.
Contact us today if you want to discuss your cybersecurity in greater detail and pinpoint potential risks. We can arrange a quick chat to discussed some options we have available that would help enhance your businesses security. Give us a call at 716-373-4467 x 15 or email us at: [email protected] to learn more.
Article used with permission from The Technology Press.
Read More

Managing Data and IT Solutions In-House can be Challenging and Expensive.
That’s why many organizations turn to MSPs.
Digitalization has forced businesses to alter their operations and make IT a huge part of their day-to-day affairs. Still, some owners choose to hire a managed service provider, or MSP, to take care of the work.
But what exactly is an MSP?
Simply put, this is a third-party company you can collaborate with to help manage parts of your business, such as your IT or cloud needs. It provides technology and expertise to boost your organization’s scalability.
Working with MSPs can have tremendous benefits for your enterprise.
For instance, their profound understanding of cutting-edge technology can help you improve performance, operations, and security while reducing overheads. In addition, they can offer several creative solutions to help you navigate the evolving landscape of the big data world.
But the strongest suit of any MSP is usually their ability to deliver tailor-made solutions that fit your company perfectly.
Their expertise allows them to analyze your business thoroughly and render their services according to your strengths and weaknesses. Plus, they consider the regulatory environment and compliance to safeguard against legal issues.
Another great thing about MSPs is that they can support your business even after hours. They offer support measures and staff to maintain and protect your organization 24/7. MSPs can even tap into your system to resolve issues and deploy updates without going to your office using remote technology.
Overall, MSPs can help take your company to the next level. However, you can’t work with just any service provider. You need to select the right team for your enterprise, and this article will show you how.
What to Look For When Choosing and MSP
Hiring an MSP shouldn’t be a hasty decision. Instead, you want to take a variety of factors into account.
Here are the six important factors to keep in mind:
Factor #1: The MSP’s Track Record
Prospective MSPs should provide case studies and success stories to demonstrate they’re suitable for your business. You can also look for testimonials, references, and endorsements. These will help you determine if the team has been operating for a while and if their reputation is solid.
Working with a reputable MSP can give you peace of mind with the knowledge that your system will be appropriately managed. Moreover, you’ll feel confident that the MSP will do all in its power to preserve its name.
The MSP’s success hinges on yours in some respect, which is why they’ll view you as a valuable partner.
Factor #2: The Range of Services it Provides
MSPs offer a wide array of services. Some teams are full-service companies, meaning they address your cloud and IT needs comprehensively. In contrast, others may help you with different pieces of your tech puzzle.
Therefore, consider your needs carefully and ensure your MSP can meet them.
Regardless of your service package, the MSP needs to keep up with the latest technology trends. Otherwise, numerous security issues may compromise your company and allow the competition to prevail over you.
Factor #3: Support
As previously indicated, MSPs can work round the clock to ensure your business is compliant and maintained adequately. However, they should also increase their support quickly and adjust staff schedules as your company grows.
That’s why you should consider an MSP that offers training for your employees.
It lets them understand the necessary changes and encourages them to train other team members as they join your business. But if your employees are too busy, you can instruct the MSP to carry out all the training.
Factor #4: Response Time
Your network can go down for any number of reasons, preventing your employees from working and your clients from reaching you. This situation can even cripple your reputation, customer base, and revenue. In the worst-case scenario, it can even make you shut down your business.
Fortunately, a high-quality MSP can help you avoid this scenario. They can identify threats to your system and neutralize them before hurting your company.
Moreover, if an incident takes place, they should respond immediately. They need to mitigate the risks as soon as possible to keep your organization from crumbling.
Factor #5: Security and Backup
One of the most important duties your MSP should perform is to shield your data from cyberattacks. This is critical to protecting your company and customers. Besides, safe data storage might be mandatory in your industry, which is why your IT department could use all the help they can get.
Once you work with an MSP, they should recommend robust security solutions and endpoint protection to combat harmful software. And throughout their engagement, they should consider compliance to help prevent legal issues.
Another major part of their mission should be the implementation of backup software. It enables you to retrieve your data in case of a breach. Such implementation may involve automation, a restoration plan, and a no-downtime policy.
With a failproof backup and security strategy in place, you should be able to run your company more confidently. The risk of downtime will be drastically lower, allowing you to operate smoothly, maintain high sales, retain customers, and preserve your brand.
Click here to learn more about our preferred data protection & business continuity solution, Datto!
Factor #6: Guidance on Workflow Options
Your MSP shouldn’t just deal with cybersecurity – they should also suggest adopting the best practices across the entire tech landscape.
For example, they should advise you on various CRM solutions and project management applications. They should also help you revamp your approach to workflow and data to create efficiency in all departments.
The fact is, you can yield tremendous results from their guidance. Your team can work faster, collaborate in real-time, and be more tech-savvy.
Recruit Your MSP Carefully
While price is important when selecting an MSP, it pales in comparison to all the factors listed above. Be sure they’re a perfect fit for your enterprise, even if you need to pay more.
With high expertise, customized services, and an understanding of threats, a reputable team can help you stay ahead of your competitors.
Article used with permission from The Technology Press.
Read More

Have You Made Cybersecurity a Priority in Your Business?
If not, I strongly urge you to do so.
Otherwise, you’ll continue to make yourself vulnerable and it’ll only be a matter of time when your business gets hacked.
Yes, it’s now a ‘when you get hacked’, not an ‘if you get hacked’ situation.
In fact, the primary reason for the numerous successful hacks on businesses can be ascribed to a lack of cybersecurity.
Business leaders can often underestimate this and make the mistake of thinking, “My business is small, why would hackers pay attention to me?”
Believe me, they still will.
Luckily, you can take steps right now to resolve that issue.
1. Invest in Cybersecurity
Investing in cybersecurity means several things, but these are the most basic:
- Direct enough resources towards making your accounts, hardware, and network safe.
- Educate your team on the dangers of cyberthreats and train them to follow security procedures. Employees are often the weakest point in your security grid, as any device they use for work can be a potential point of entry for hackers.
2. Leverage Two-Factor Authentication, or 2FA
It’s a highly effective solution to preventing hacker attacks. This method works by requesting confirmation before the user can log into their account.
Encourage your employees to use 2FA on both work and personal accounts.
3. Use EndPoint Protection Software
It may sound old-school, but it’s still an excellent method of cyber-attack prevention. But to ensure maximum cybersecurity for your business, purchase a professional package.
Please contact us at you’d like to learn more about using advanced cybersecurity methods for your business. We can arrange a quick chat to discussed some options we have available that would help protect your business. Give us a call at 716-373-4467 x 15 or email us at: [email protected] to learn more.
Article used with permission from The Technology Press.
Read More

Education: Bachelor’s degree in environmental sciences and Ecology from SUNY Brockport.
How did you get into the technology field? This is my first job position in a technology field.
When did you join the Databranch team? January of 2022
What do you like best about Databranch? The work environment. You immediately feel like part of a family that genuinely cares about your personal and professional development.
How would you describe your role at Databranch? As the Databranch Sales and Marketing Coordinator, I work directly with our sales/marketing team to help our clients keep their business data protected, stay secure, and maximize their technology investments.
What’s an interesting way that you use technology in your personal life? I enjoy the voice activated smart appliances around my home which allow me to turn on/off lights, coffee makers, etc.
How many computers do you own? Just one laptop.
Hobbies: During the summer you can often find me hiking. In the winter I keep busy by reading, puzzling, and snowboarding.
Pets: None right now but I hope to adopt a few cats in the future.
Read More
Conducting business operations in the digital world is prone to security risks. Mitigating them would be impossible if you don’t have an IT compliance policy.
Setting up a robust IT compliance policy in your business is more important now than ever and it’s because most organizations now depend on digitized services.
Online companies rely on e-commerce websites to do business by taking orders and receiving payments. Even brick-and-mortar organizations utilize software to perform various activities, such as order management and back-office accounting.
In such tech-driven environments, a lack of proper security measures jeopardizes the business leader’s position. Their IT systems get abused and their technology often becomes a source of scandals.
The only way to avoid this possibility is to create a strong IT compliance policy.
This article will cover key considerations when developing your system of IT compliance and how Databranch can help you implement an IT compliance policy.
WHAT YOU NEED TO CONSIDER FOR IT COMPLIANCE POLICIES
FACTOR #1 – PEOPLE, PROCESSES, AND HOW THEY ALIGN TO TECH
IT compliance isn’t just about technology – it also involves people and processes. And the reality is that many organizations focus heavily on their tech, resulting in failed audits due to their failure to consider the other two aspects. This makes the compliance world more complex.
Taking the correct approach can help ensure your enterprise abides by the necessary standards.
FACTOR #2 – RELEVANT LAWS AND REGULATIONS
Laws and regulations stipulate the policies that govern IT compliance requirements. Here are the most common ones:
- The Sarbanes-Oxley Act – regulating financial reporting
- The Gramm-Leach-Bliley Act – governing non-public personal information and financial data
- The Health Insurance and Accountability ACT – regulating health information that healthcare organizations process
Ultimately, you can’t start your compliance process without understanding the laws and regulations applicable to your organization.
You should also ascertain the controls that apply to these laws and regulations. They are process-oriented and technical means to adhere to your policies.
There are various industry and government standards that specify them, including:
- Control Objectives for Information and Related IT
- National Institute of Standards and Technology
- Payment Card Industry Data
These can have a massive bearing on your sector. Therefore, make sure to familiarize yourself with all relevant controls.
FACTOR #3 – RAISING EMPLOYEE AWARENESS OF THE IMPORTANCE OF THE POLICY
One of the biggest threats to your data security is having untrained employees. Their actions can have a huge impact on cybersecurity. For instance, improper software upload, sharing, download, and storing can jeopardize critical information.
The reality is, many employees opt for insecure data transfer methods due to their convenience. Some of the tools they use are personal emails, consumer-grade collaboration apps, and instant messaging. All of these are ideal targets for cyber criminals.
To prevent your business from becoming a victim, your users must learn and understand where various threats originate from. They should especially understand the actions that can give rise to vulnerabilities.
Making file sharing a top priority and investing in proper education demonstrates the significance of IT compliance. Your efforts can help team members willing to adopt the best practices in this field.
When developing your training plan, make sure to include several key topics:
- How insecure file transfer methods expose your company to risks
- Avoiding phishing scams
- Precautions to exercise before using or downloading unsanctioned applications
- The conditions for using and creating strong passwords.
FACTOR #4 – HOW YOUR IT POLICY ALIGNS WITH THE COMPANY’S SECURITY POLICIES
Aligning IT compliance with your business operations involves understanding the culture of your organization. For example, your environment can revolve around either processes or ad-hoc ways of doing things.
Enterprises aligning with the former are best off issuing in-depth policies to ensure compliance.
By contrast, companies that match the latter require detective and preventive controls. They need to address specific risks associated with your policy. It helps various auditors understand why you’ve deployed a particular control or decided to face certain risks.
FACTOR #5 – UNDERSTANDING OF THE IT ENVIRONMENT
IT environments directly affect your IT policy compliance design. That said, there are two main kinds of environments:
- Homogeneous environments – These consist of standardized vendors, configurations, and models. They’re largely consistent with your IT deployment.
- Heterogeneous environments – The other type uses a wide range of security and compliance applications, versions, and technologies.
Generally, compliance costs are lower in homogeneous environments. Fewer vendors and technology add-ons provide less complexity and fewer policies. As a result, the price of security and compliance per system isn’t as high as with heterogeneous solutions.
Regardless of your environment, your policy needs to appropriately tackle new technologies, including virtualization and cloud computing.
FACTOR #6 – ESTABLISHMENT OF ACCOUNTABILITY
IT policy compliance doesn’t function without accountability. It entails defining organizational responsibilities and roles that determine the assets individuals need to protect. It also establishes who has the power to make crucial decisions.
Accountability begins from the top and encompasses executives and the best way to guarantee involvement is to cast IT policy compliance programs in terms of risks instead of technology.
As for your IT providers, they have two pivotal roles:
- Data/system owners – The owner is part of your management team that’s responsible for data usage and care. Plus, they’re accountable for protecting and managing information.
- Data/system custodians – Custodial roles can entail several duties, such as system administration, security analysis, legal counseling, and internal auditing.
These responsibilities are essential for IT policy compliance. For example, auditors need to carefully verify compliance activity execution. Otherwise, there’s no way to ensure the implementation is going according to plan.
FACTOR #7 – AUTOMATION OF THE COMPLIANCE PROCESS
Your IT continually evolves and grows. Internal auditors can only review a small number of user accounts and system configurations.
Automation is the only way to ensure you can evaluate enough systems regularly.
BREEZE THROUGH YOUR BUSINESS’S IT COMPLIANCE
Setting up well-designed IT compliance may be a long process, but it can make a world of difference in terms of business security. It keeps your business reputation intact and allows you to avoid penalties and fines.
However, you’ll need to pay special attention to several aspects and one of the most significant ones is your IT provider.
If your IT isn’t living up to its potential, you’re bound to face compliance issues. This can cause tremendous stress and halt your operations.
Luckily, there might be an easy way out of your predicament. Schedule a quick chat with Databranch to discuss your IT problems and find out how to get more out of your provider.
Article used with permission from The Technology Press.
Read More

IMAGE SOURCE: https://www.office.com/
There are numerous suites of apps that can improve your productivity. One of them is Office 365, which features an array of underappreciated tools.
Office 365 has helped millions of organizations streamline their operations. One of the most famous examples involves Kohler, the manufacturer of kitchen and bath fixtures and plumbing.
At the start of the coronavirus pandemic, they struggled to manage operations since most of their team had to work remotely. The company had to adjust its activities to stay true to its values.
That’s where Office 365 came into play.
It helped them deliver personalized training in a short period. Their employees gained access to curated podcasts, Q&A sessions, micro-learning videos, and renowned experts. All of which helped them become more comfortable with their new suite of apps.
Over time, the platform also enabled them to overcome the limitations of cultures, languages, and time zones with different tools.
For instance, they used Teams to mobilize professionals who shared insights into worldwide markets. Likewise, SharePoint facilitated the movement of over 400 terabytes of directories, expediting customer communication and support. The enterprise also enhanced its security and device deployment, creating a seamless culture of agility and productivity.
It’s worth mentioning that Office 365 isn’t just suitable for large companies like Kohler. Any business leader can leverage this productivity suite to increase productivity. The reality is that many of these tools are underused and underappreciated.
This article will highlight some of the top Office 365 tools you should consider implementing in your business.
THE TOOLS
TOOL #1 – FLOW
Microsoft Flow enables you to automate your workflow across various applications. You can connect it to instant message and email alerts, synchronize files from different apps or copy them from one platform to another.
For example, if you fill out a SharePoint form, you can use Flow to develop a lead in Dynamics 365.
Best of all, the tool isn’t limited to Microsoft Services. It lets you extract data from Facebook or upload files to Dropbox. The result is higher productivity through improved connections.
TOOL #2 – TEAMS
Teams is a meeting, sharing, and chatting hub for your team. This cloud-based platform combines notes, files, conferences, and several apps in real-time.
The program has dramatically improved collaboration and productivity, bringing people, content, and conversations together into a single hub. It integrates effortlessly with Office 365 apps and features a secure global cloud.
Another tremendous benefit is real-time communication. It lets all members watch edits in PowerPoint presentations, ensuring input from the entire team. Users can also provide feedback using the chat window to streamline productivity.
In addition, Teams supports cross-platform cooperation, allowing you to work on your phone, tablet, or computer.
TOOL #3 – TO-DO
Microsoft To-Do is a smart task management platform that facilitates planning throughout your day. Not to mention it delivers a personalized and intuitive way to help users stay organized.
It comes with a robust algorithm that lets you create lists for nearly anything, such as your home projects, work, and grocery shopping.
Keeping track of reminders is effortless with To-Do. You can add reminders, notes, and due dates while personalizing them with vivid themes. Aside from viewing them on the web, these lists are also accessible on most devices, including Android phones, iPhones, and Windows 10 devices.
TOOL #4 – MYANALYTICS
Although teams spend much of their time in meetings, talking on the phone, and sending emails, they still may not be very productive. To overcome this obstacle, Office 365 introduced MyAnalytics.
This tool increases employee efficiency by analyzing two productivity factors: who users spend their time with and how they spend it.
Using robust analytics, the tool suggests how you can be more productive by working less after-hours and reducing idle meeting time. There’s also AI that flags your Outlook commitments to remind you of your daily duties.
MyAnalytics consists of four components:
- Digests – Your Outlook inbox stores weekly digests to highlight the previous week.
- Dashboard – The dashboard displays various statistics like productivity insights, work habits, and suggestions on improving them.
- Insights Outlook – This feature presents cards that show your work experience and allow you to respond in many ways.
- Inline Suggestions – These suggestions are available in your Outlook to help boost productivity.
Also, Microsoft considered your privacy when designing this tool. That’s why you’re the only one who can access your personal insights and data.
TOOL #5 – VIVA
Microsoft Viva is an employee experience platform that helps to improve learning, well being, and collaboration in the workplace. The tool consists of four modules: Viva Topics, Viva Connections, Viva Insights, and Viva Learning.
Viva Topics gathers and organizes content and knowledge around any topic in a business using Microsoft Graph and AI.
Viva Connections works as a SharePoint app within Teams, allowing you to share curated news and articles with your employers.
Viva Insights provides insight into employees’ work patterns that can cause stress and burnout, such as meeting overload and regular after-hours work. The app enables managers to help their teams find a balance between well being and productivity.
Viva Learning is a learning hub in Teams that makes it easy for you to share learning content and training resources across your business.
TOOL #6 – DELVE
This is a nifty visualization tool that incorporates social media elements and social learning. It utilizes content from four platforms: Exchange, SharePoint, Yammer, and One Drive,
However, it doesn’t aggregate your data points only. Instead, it detects relevant information like user activity and past interactions.
TOOL #7 – SWAY

IMAGE SOURCE: https://sway.office.com/
Sway is a presentation app that might someday replace PowerPoint. It boasts an integrated design engine to produce appealing presentations and reports.
Some of the features include dragging and dropping images, charts, videos, and canvas-based formats. The program can also produce newsletters and stories that can be viewed on various devices.
TOOL #8 – PLANNER
Microsoft Planner is an excellent choice for companies with team members all over the globe and multiple simultaneous projects. The tool can rapidly digitize your task management processes.
It gives users access to visual organization tools and four key functions: information hub, insights, communication, and flexible categorizations. Also, it enables team members to share files, create plans, assign and assemble tasks, and converse with co-workers while receiving progress updates.
REINVIGORATE YOUR BUSINESS’S WORK ENVIRONMENT
Taking your operations to new heights is all about creating an agile and productive workplace. And Office 365 can help you achieve this with a wide range of communication and collaboration tools.
Whether your team works remotely or in-office, this suite of apps can dramatically improve project management. And Kohler’s example is proof of this.
That said, a subpar IT provider can impede your integration with Office 365.
If you feel your vendor isn’t delivering the necessary results, give Databranch a call at 716-373-4467 x 15 or email us at: [email protected].
We can schedule a quick chat and come up with the perfect solution to your business’s IT difficulties to save you from a lot of stress.
Article used with permission from The Technology Press.
Read More

IMAGE SOURCE: https://unsplash.com/photos/dpbXgTh0Lac
Increasing productivity in your business doesn’t just entail optimizing your equipment and sharpening your attention. Decluttering your computer desktop is also essential.
A clutter-free office is paramount to improving your productivity. Piles of stationery on your desk can cause you to waste a lot of time searching for a critical document. As a result, you’re less likely to meet deadlines.
Clutter can affect you in various indirect ways, too.
It can dramatically reduce your cognitive abilities, impairing your decision-making and relationships with your team members. In addition, it can have an adverse effect on your anxiety, focus, sleep, and eating choices. All of these can reduce your workplace performance.
However, this clutter problem doesn’t just affect your desk or office.
Your computer desktop can also be cluttered. Disorganized folders and a lackluster display impact your productivity as much as physical clutter. To avoid this scenario, you need to declutter your computer as well.
This article will share seven tips on decluttering your computer desktop.
THE 7 TIPS
TIP #1 – DEVELOP A FOLDER SYSTEM WITH FILE NAMING CONVENTIONS
The most important thing you should do to prevent clutter on your computer is set up an intuitive folder system. You can use several categories, such as file type or name, depending on what suits your research or work best.
Regardless of your approach, be sure to choose well-established naming conventions that let you quickly navigate through your documents. The system should also be easy to use for many years to come, so consider your plans when creating it.
You can place these folders in your file share tools (e.g., Google Drive and Dropbox), hard drive, or desktop if you back them up regularly.
With a fully functional structure, you can bypass your desktop by simply downloading new documents to designated folders. Afterward, you can rapidly locate them with the search command on your computer. Type in the name of your folder, and you’ll reach the desired file within seconds.
TIP #2 – MAKE YOUR DESKTOP ATTRACTIVE TO YOU
Besides making your computer desktop fully functional, you should also enhance its appeal. So, select a meaningful or beautiful background. It needs to be enjoyable to look at, motivating you to keep your computer tidy.
To take the aesthetics to the next level, set gridded or lined images as the background to organize files that end up there more easily.
Another great idea is to use a motivational background. Images with powerful messages encourage you to work harder and remain focused. This type of coaching also enables you to organize your desktop and stay on top of clutter.
TIP #3 – CONSIDER SECTIONED DESKTOP WALLPAPER
Sectioned desktop wallpapers are a great way to enhance your desktop organization further. For instance, you can include a section for your vacation or pets.
There are millions of wallpapers online that can help you declutter your desktop. They complement folder naming conventions to improve your workflow.
TIP #4 – CONSOLIDATE YOUR MOST USED APPS/SOFTWARE
Having quick access to your most used programs or software is a must. It allows you to start working immediately without wasting time searching for apps.
To consolidate efficiently, you should first determine which software matters most to you. Your portfolio may comprise two or three apps you use daily or an entire suite of programs that provide the necessary functionality.
Once you’ve assembled your list, you may be able to merge multiple programs with a comprehensive solution. It puts them in one place to streamline your productivity.
The taskbar is an effective alternative, as program icons are often responsible for the bulk of your clutter. Keeping the essential icons in the taskbar makes them quickly accessible since you won’t need to browse.
TIP #5 – DELETE OR RELOCATE UNUSED FILES

IMAGE SOURCE: https://unsplash.com/photos/HjBcAVWlxnE
After categorizing vital apps, you also need to address unused programs. Here’s a tip: if you can’t recall when you last used certain software, uninstall it. Do the same if you don’t think you’ll need a particular application for an upcoming project.
Since this may be a hard decision, you may want to create a folder for these rarely used apps and files instead. Tuck them away until you figure out if you wish to proceed with the deletion.
For this wait-and-see approach, you can make use of several folders, such as “miscellaneous” or “to be archived.” In doing so, you won’t accidentally uninstall or remove a crucial program.
Now, if you take this approach, make sure to check the folders regularly. Determine which files and apps are no longer needed in your business and delete them to avoid clutter.
To avoid falling behind with your cleaning, set a reminder on your calendar. It can be a monthly or weekly event, depending on your workload.
TIP #6 – CATEGORIZE NEW CONTENT
Dumping new files and programs onto your desktop may be tempting if you’re in a hurry. However, this method is ill-advised because it inhibits your organization.
Try to allocate a few minutes to organize all new apps and files appropriately, according to your naming conventions. A quick way to do so is to use automatic file sorting by date or alphabetically. It doesn’t take long, yet it can significantly reduce clutter on your computer.
TIP #7 – EMPLOY FENCES
Digital fences group files in specific regions of your desktop to make them more visually accessible. This method works much better than burying all your files in one or two folders. Plus, many people consider it more user-friendly than gridded backgrounds.
For example, the Stacks feature automatically categorizes content by type or any other specific feature. It’s available for free on Macs with Mojave.
Likewise, PCs have a similar feature called Fences. It enables you to designate and move fences around the desktop for improved maneuverability. The only downside to this is that it’s not free.
DON’T LET CLUTTER GET OUT OF HAND
Decluttering your computer desktop is one of the best ways to advance your productivity.
Once you’ve organized it appropriately, you’ll be able to find the necessary files and programs effortlessly. You’ll then feel rejuvenated, and your mood may improve dramatically, allowing you to overcome mental obstacles during your workday.
It might take some time to optimize your desktop, but it’ll be well worth it.
You can also assign this job to your IT provider. However, they may not understand your needs and that of your business correctly, and their services might be insufficient.
In that case, let’s have a 10-15-minute chat and see if Databranch can resolve your problem. Give us a call at 716-373-4467 x 15 and we’ll do all we can to help you increase office productivity in your business.
Article used with permission from The Technology Press.
Read More
 IMAGE SOURCE: https://pixabay.com/photos/cyber-security-internet-network-4610993/ An effective way to bolster your business’s data security is to work with a Managed Service Provider (MSP) or I.T. Service Provider (ITSP) like Databranch. They address network vulnerabilities to prevent cyber criminals from exploiting them.
Besides monitoring and organizing your servers, a Managed Service Provider (MSP) or I.T. Service Provider (ITSP) plays a pivotal role in the cybersecurity program of your business. They implement several strategies to shield your network from attacks and protect your data.
For instance, many providers use email authentication protocols to monitor your server’s vulnerabilities. They can keep users from accidentally accessing malicious websites by determining spam emails containing malware or viruses. This results in enhanced system security.
Another common practice is training your employees to ensure they follow the highest security standards. This is especially important if you have remote team members since there’s no way to keep track of their activities. To tackle this issue, an MSP or ITSP teaches your staff how to operate safely to avoid harm to your company’s infrastructure and reputation.
On top of that, an MSP or ITSP can neutralize various threats due to their proactive approach. They offer several tools such as firewalls and endpoint detection to control the traffic and stave off cyber attacks. Also, they can install antivirus software and email security to stop intrusion attempts.
Needless to say, an MSP or ITSP can shield you from a wide array of cybersecurity issues. But it’s vital to work with the right provider.
To ensure this happens, you should look for and abide by the best practices for an MSP or ITSP in the cybersecurity space. This article will examine what they are.
THE 8 BEST PRACTICES
PRACTICE #1 – ENFORCE MULTI-FACTOR AUTHENTICATION (MFA)
Cybercriminals are becoming proficient at accessing your credentials, so it’s critical to enable MFA for all your users.
It consists of three elements: a password, security token, and biometric verification. Consequently, if attackers breach one security layer, they’ll still have to do a lot of digging to access your information.
PRACTICE #2 – MAKE PATCHING A PRIORITY
Application and operating system exploits are common. Hackers target them to access your system and compromise your data, but you can prevent this through regular patching.
Making sure your system is up to date with the latest security standards decreases the risk of exploitation.
PRACTICE #3 – CONDUCT REGULAR CYBERSECURITY AUDITS
An MSP or ITSP must be aware of on boarding, off boarding, and lateral movements within an organization. This warrants frequent cybersecurity audits to assess the competency of your team.
Many MSPs or ITSPs hire third-party companies to perform their security audits. They can detect if a person who no longer needs access to the network still has it. It’s something that can endanger the client’s information, especially if the individual is a former employee.
Conducting regular audits mitigates this risk. It enables an MSP or ITSP to implement some of the most effective access privilege limitations:
- IP restrictions – These security measures ensure that only users who can access your local network can utilize remote administration tools.
- RMM software updates – Software vendors typically dispatch updates to fix vulnerabilities and patch numerous security gaps.
- RDP (Remote Desktop Protocol) Security – This Windows native administration tool reduces the chances of ransomware attacks in your organization.
PRACTICE #4 – HAVE AN OFF-SITE BACKUP
Backups are crucial for tackling malicious activities and ensuring operational continuity after cyber attacks.
They also help address whether the company and its clients can access the latest version of their data and applications. This feature is vital for enterprises that must adhere to compliance requirements, including PCI-DSS and HIPAA.
But besides implementing on-site backups, your MSP or ITSP should also set up off-site versions. If attackers compromise your RMM software, they can most likely reach on-site backups, too.
So, to avoid disasters, businesses should have an off-site backup accessible to only a few people. It should also be offline for greater security.
(Databranch is a proud Datto Diamond Partner and can help your organization implement a true business continuity/data protection solution for your organization.)
PRACTICE #5 – INCORPORATE LOG MONITORING
 IMAGE SOURCE: https://pixabay.com/photos/startup-business-people-students-849804/ Log monitoring is analyzing your logs for potential glitches. As an MSP or ITSP scrutinizes your records, they can detect traffic from harmful sources and provide a clear idea of threat patterns. And over time, they can deploy countermeasures to seal these gaps.
For example, cybersecurity experts use reliable security information and event management (SIEM) tools. They facilitate scanning through piles of information to enable faster threat detection.
PRACTICE #6 – LAUNCH PHISHING CAMPAIGNS
Phishing cyber criminals target your team members with emails or text messages, posing as legitimate institutions to steal your data. Unfortunately, most attacks succeed because of human error, meaning your MSP or ITSP should be aware of and monitor employees’ behavior.
Setting up fake phishing campaigns is a great way to test your team’s ability to respond to phishing attacks. It allows you to pinpoint and improve inadequate responses, bolstering data security.
To learn more about Databranch’s Breach Prevention Platform which includes monthly simulated phishing attempts and continuous end-user security awareness training, click here or email: [email protected]
PRACTICE #7 – CHOOSE YOUR SOFTWARE CAREFULLY AND SECURE ENDPOINTS
From small browser plugins to large-scale business systems, be sure your providers take data protection and cybersecurity seriously. Learn about their commitment to these aspects before purchasing their application.
Furthermore, employ web filtering tools, antivirus software, and email authentication to fend off ransomware attacks through malicious emails. Ensure each endpoint and your virus definition library are secure and up to date with the latest standards.
PRACTICE #8 – SET ALERTS AND DOCUMENT EVERYTHING
An MSP or ITSP that configures their systems to receive alerts upon system changes can work proactively and tackle threats early on. Many platforms automate this process through rules templates, personalization, and direct tickets to the PSA. This eliminates manual digging, saving precious time.
Another useful strategy is to document your cybersecurity information, such as your defense mechanisms, emergency guidelines, and disaster recovery plans. You should also review it regularly to help preempt cyber attacks.
CYBERSECURITY IS PARAMOUNT
While digitalization has significantly streamlined your operations, it’s also made you more susceptible to data theft.
To ensure cyber criminals don’t get their hands on valuable information and ruin your reputation, your MSP or ITSP needs to adopt well-established security practices.
But if your provider hasn’t introduced off-site backups, regular patches, and employee training, you’re not getting your money’s worth. Hence, you may be frustrated since your provider isn’t delivering the necessary results.
This makes you a sitting duck for cyber criminals. You need to resolve the issue as soon as possible.
Databranch can help you do so. Reach out to us for a quick 15-minute chat at 716-373-4467 x 15 and our tech experts will do their best to show you a way out of your cybersecurity dead end.
Article used with permission from The Technology Press.
|
Read More






















