
Databranch has been tracking a Microsoft Outlook security flaw, CVE-2023-23397.
The critical Outlook exploit affects both 32 and 64-bit versions of Microsoft 365 Apps for Enterprise. Office 2013, 2016, and 2019.
It is triggered by sending a malicious email (which doesn’t even need to be opened) that lets attackers capture the Net-NTLMv2 hash (challenge response protocols used for authentication in Windows environments) of the recipient and thereby authenticate as the victim.
More information can be found here.
Microsoft has released a patch to address some instances of Outlook.
If you are a managed maintenance client, we are actively working to patch vulnerable instances of Outlook for you.
You may see the following prompts as your client is updated.
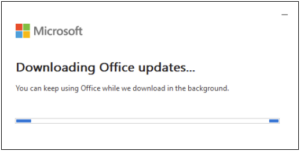
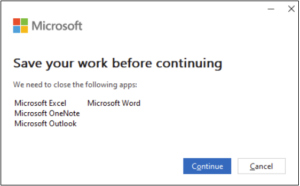
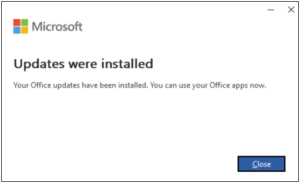
Please feel free to reach out to [email protected] with any questions.
If you are not a managed client and would like to discuss how Databranch can help to proactively manage, monitor, and patch your IT environment, please reach out to Databranch at 716-373-4467 x115 or [email protected].
comments powered by Disqus