
Cybersecurity is an essential aspect of any business or organization. As technology evolves, so do the threats that can harm an organization’s operations, data and reputation. One of the most effective ways to defend against these threats is through the Defense in Depth (DiD) approach.
DiD is a cybersecurity approach in which multiple defensive methods are layered to protect a business. Since no individual security measure is guaranteed to endure every attack, combining several layers of security is more effective.
This layering approach was first conceived by the National Security Agency (NSA) and is inspired by a military tactic with the same name. In the military, layers of defense help buy time.
However, in IT, this approach is intended to prevent an incident altogether.
Essential Elements of DiD
Implementing all the elements of an effective DiD strategy can help minimize the chances of threats seeping through the cracks. These elements include:
1. Firewalls
A firewall is a security system comprised of hardware or software that can protect your network by filtering out unnecessary traffic and blocking unauthorized access to your data.
2. Intrusion Prevention and Detection Systems
Intrusion prevention and detection systems scan the network to look for anything out of place. If a threatening activity is detected, it will alert the stakeholders and block attacks.
3. Endpoint Detection and Response (EDR)
Endpoint detection and response (EDR) solutions constantly monitor endpoints to find suspicious or malicious behavior in real time.
Databranch is excited to announce a new detection software that we have begun implementing for our clients. The Huntress Managed Detection and Response (MDR) for Microsoft 365 secures your users with 24/7 protection.
Huntress MDR can detect and respond to early signs of cyberattacks such as unauthorized access, email manipulation, and suspicious login locations.
The software then utilizes Huntress’s 24/7 Security Operations Center (SOC) which is comprised of experts who analyze and interpret the threats. An actual Huntress employee will review these detections, provide incident reports, and will deliver actionable remediations for recovery.
4. Network Segmentation
Once you divide your business’s network into smaller units, you can monitor data traffic between segments and safeguard them from one another.
5. The Principle of Least Privilege (PoLP)
The principle of least privilege (PoLP) is a cybersecurity concept in which a user is only granted the minimum levels of access/permissions essential to perform their task.
Visit us here to learn more about the risks associated with Local Administrative Privileges.
6. Strong Passwords
Poor password hygiene, including default passwords like “1234” or “admin,” can put your business at risk. Equally risky is the habit of using the same passwords for multiple accounts.
To protect your accounts from being hacked, it’s essential to have strong passwords and an added layer of protection by using practices such as Multi-Factor Authentication (MFA).
7. Patch Management
Security gaps left unattended due to poor patch management can make your business vulnerable to cyberattacks. When a new patch is delivered, deploy it immediately to prevent exploitation.
Databranch offers a Patch Management solution for our managed client’s that automates and manages service packs, hot-fixes, and patches from a single location.
How IT service providers help defend against threats
As a Databranch client, our experienced team members will help you divide DiD into three security control areas:
1. Administrative controls
The policies and procedures of a business fall under administrative controls. These controls ensure that appropriate guidance is available and security policies are followed.
Examples include hiring practices or employee onboarding protocols, data processing and management procedures, information security policies, vendor risk management and third-party risk management frameworks, information risk management strategies, and more.
3. Technical controls
Hardware or software intended to protect systems and resources fall under technical controls.
They include firewalls, configuration management, disk/data encryption, identity authentication (IAM), vulnerability scanners, patch management, virtual private networks (VPNs), intrusion detection systems (IDS), security awareness training and more.
4. Physical controls
Anything that physically limits or prevents IT system access falls under physical controls, such as fences, keycards/badges, CCTV systems, locker rooms and more.
Don’t worry if you are struggling with developing a DiD strategy for your organization. Databranch is here to make things as simple as possible. Contact us at 716-373-4467 option 6, or [email protected] to start the process of making your organization more secure.
Read More

Social media has significantly transformed the way we communicate and do business. However, this growing popularity also comes with potential risks that could cause harm to businesses like yours.
Unfortunately, many organizations remain unaware of these rapidly evolving challenges. In this blog, we will explore the dangers associated with social media and share practical tips to safeguard your organization’s reputation and financial stability so that you can safely reap the benefits of social media platforms.
Exploring the Risks
Social media presents several risks that you need to address, such as:
Security Breaches
Cybercriminals can exploit social media to steal sensitive information by creating fake profiles and content to trick people into sharing confidential data. Social media platforms are also vulnerable to hacking, which can have a negative impact on your business.
Reputation Damage
Negative comments from dissatisfied customers, envious competitors or even unhappy employees can quickly spread online and cause significant damage to your brand’s image within seconds.
Employee Misconduct
Certain employees may share offensive content or leak confidential information on social media, which can trigger a crisis that can be challenging for business leaders to handle.
Legal Accountability
Social media has the potential to blur the boundaries between personal and professional lives, which can, in turn, create legal liabilities for your business. If your employees make malicious remarks about competitors, clients or individuals, the public can hold you responsible for their actions. Employees may also face the consequences if their social media behavior violates the organization’s regulations.
Phishing Threats
Social media phishing scams can target your business and employees by installing malware or ransomware through seemingly authentic posts.
Fake LinkedIn Jobs
Cybercriminals often pose as recruiters on LinkedIn and post fake job listings to collect data for identity theft scams.
Securing Your Business
Taking proactive measures is essential to avoid social media risks, including:
Checking Privacy Settings
Set privacy settings to the highest level across all accounts, restricting your and your employees’ access to sensitive information. This includes removing Local Admin Privileges for employees.
Strengthening Security
Employ robust passwords and multifactor authentication (MFA) to bolster account security.
Establishing Clear Guidelines
Enforce clear social media rules for company and personal devices, customizing policies to fit your industry’s unique risks.
Educating Your Teams
Educate your team on social media risks, imparting safe practices to thwart scams and phishing attempts. Our Employee Cybersecurity Training not only offers an annual cybersecurity training, but also contains weekly micro-trainings to keep your employees up to date on real world threats.
Identifying Impersonation
Develop protocols to detect and manage fake profiles and impersonations swiftly. Remain vigilant and report any suspicious activity.
Vigilant Monitoring
Set up a system to monitor social media, promptly addressing fraudulent accounts or suspicious activity that could stain your brand image.
Act Now to Safeguard Your Business
Understanding the risks and adhering to social media best practices are crucial for businesses of all sizes. By following these guidelines, you can reduce your business’s vulnerability while reaping the rewards of social media.
For comprehensive insights into social media safety, download our eBook “From Vulnerability to Vigilance: Social Media Safety.”
Reach out to Databranch today at 716-373-4467 option 4 or [email protected] if your business is looking to increase their cybersecurity awareness.
Read More

In recent years, email has become an essential part of our daily lives. Many people use it for various purposes, including business transactions. With the increasing dependence on digital technology, cybercrime has grown. A significant cyber threat facing businesses today is Business Email Compromise (BEC).
Why is it important to pay particular attention to BEC attacks? Because they’ve been on the rise. BEC attacks jumped 81% in 2022, and as many as 98% of employees fail to report the threat.
What is Business Email Compromise (BEC)?
Business Email Compromise (BEC) is a type of scam in which criminals use email fraud to target victims. These victims include both businesses and individuals. They especially target those who perform wire transfer payments.
The scammer pretends to be a high-level executive or business partner and will send emails to employees, customers, or vendors. These emails request them to make payments or transfer funds in some form.
According to the FBI, BEC scams cost businesses around $1.8 billion in 2020. That figure increased to $2.4 billion in 2021. These scams can cause severe financial damage to businesses and can also harm their reputations.
How Does BEC Work?
BEC attacks are usually well-crafted and sophisticated, making it difficult to identify them. The attacker first researches the target organization and its employees. They gain knowledge about the company’s operations, suppliers, customers, and business partners.
Much of this information is freely available online. Scammers can find it on sites like LinkedIn, Facebook, and organizations’ websites. Once the attacker has enough information, they can craft a convincing email. It’s designed to appear to come from a high-level executive or a business partner.
The email will request the recipient to make a payment or transfer funds. It usually emphasizes the request being for an urgent and confidential matter. For example, a new business opportunity, a vendor payment, or a foreign tax payment.
The email will often contain a sense of urgency, compelling the recipient to act quickly. The attacker may also use social engineering tactics. Such as posing as a trusted contact or creating a fake website that mimics the company’s site. These tactics make the email seem more legitimate.
If the recipient falls for the scam and makes the payment, the attacker will make off with the funds. In their wake, they leave the victim with financial losses.
How to Fight Business Email Compromise
BEC scams can be challenging to prevent, but there are measures businesses and individuals can take to cut the risk of falling victim to them.
Educate Employees
Organizations should educate their employees about the risks of BEC, along with how to identify and avoid these scams. This includes employees recognizing tactics used by scammers such as: urgent requests, social engineering, and fake websites.
Training should also include email account security, including:
- Checking their sent folder regularly for any strange messages
- Using a strong email password with at least 12 characters
- Changing their email password regularly
- Storing their email password in a secure manner
- Notifying an IT contact if they suspect a phishing email
Contact Databranch today if your company lacks on-going cybersecurity training. Our Breach Prevention Platform and Security Awareness Training will give your employees the resources they need to spot real world phishing attempts.
Enable Email Authentication
Organizations should implement email authentication protocols.
This includes:
- Domain-based Message Authentication, Reporting, and Conformance (DMARC)
- Sender Policy Framework (SPF)
- DomainKeys Identified Mail (DKIM)
These protocols help verify the authenticity of the sender’s email address and can also reduce the risk of email spoofing. Another benefit is to keep your emails from ending up in junk mail folders.
Deploy a Payment Verification Process
Organizations should deploy a payment verification processes, such as two-factor authentication. Another protocol is confirmation from multiple parties when making a business related payment. This ensures that all wire transfer requests are legitimate. It’s always better to have more than one person verify a financial payment request.
Establish a Response Plan
Organizations should establish a response plan for BEC incidents. This includes procedures for reporting the incident as well as freezing the transfer and notifying law enforcement.
Use Anti-phishing Software
Businesses and individuals can use anti-phishing software to detect and block fraudulent emails. As AI and machine learning gain widespread use, these tools become more effective.
The use of AI in phishing technology continues to increase. Businesses must be vigilant and take steps to protect themselves.
Here at Databranch, our managed clients have the comfort of knowing that their systems are monitored and maintained on a 24/7 basis. Our tool-stack not only increases your protection from malware and phishing, but is also capable of detecting a breach in you network and isolating that device.
Enable Multi-Factor Authentication (MFA)
BEC can occur when a hacker gains access to your email’s login credentials. However, here are many valuable tools you can use to fend off these bad actors even after they have stolen your credentials.
According to a study cited by Microsoft, MFA is proven to prevent approximately 99.9% of fraudulent sign-in attempts.
This is because MFA adds a layer of cybersecurity protection by confirming the authenticity of users who are logging in to various platforms. This is completed by entering a code from your mobile device into the application you are trying to log into, or by approving a prompt that is sent to your mobile device.
This means that unless the hacker also has your mobile device, they will not be able to approve the login attempt.
Reach out to Databranch today if your interested in setting MFA up for your business accounts.
Need Help with Email Security Solutions?
It only takes a moment for money to leave your account and be unrecoverable. Don’t leave your business emails unprotected. Get in touch today at 716-373-4467 x115 or [email protected] to discuss our email security solutions.
Article used with permission from The Technology Press.
Read More

Cloud account takeover has become a major problem for organizations. Think about how much work your company does that requires a username and password.
Employees end up having to log into many different systems or cloud apps.
Hackers use various methods to get those login credentials. The goal is to gain access to business data as a user as well as launch sophisticated attacks, and send insider phishing emails.
How bad has the problem of account breaches become? Between 2019 and 2021, account takeover (ATO) rose by 307%.
Doesn’t Multi-Factor Authentication Stop Credential Breaches?
Many organizations and individuals use multi-factor authentication (MFA). It’s a way to stop attackers that have gained access to their usernames and passwords. MFA is very effective at protecting cloud accounts and has been for many years.
But it’s that effectiveness that has spurred workarounds by hackers. One of these nefarious ways to get around MFA is push-bombing.
How Does Push-Bombing Work?
When a user enables MFA on an account, they typically receive a code or authorization prompt of some type. The user enters their login credentials. Then the system sends an authorization request to the user to complete their login.
The MFA code or approval request will usually come through some type of “push” message. Users can receive it in a few ways:
- SMS/text
- A device popup
- An app notification
Receiving that notification is a normal part of the multi-factor authentication login. It’s something the user would be familiar with.
With push-bombing, hackers start with the user’s credentials. They may get them through phishing or from a large data breach password dump.
They take advantage of that push notification process. Hackers attempt to log in many times. This sends the legitimate user several push notifications, one after the other.
Many people question the receipt of an unexpected code that they didn’t request. But when someone is bombarded with these, it can be easy to mistakenly click to approve access.
Push-bombing is a form of social engineering attack designed to:
- Confuse the user
- Wear the user down
- Trick the user into approving the MFA request to give the hacker access
Ways to Combat Push-Bombing at Your Organization
Educate Employees
Knowledge is power. When a user experiences a push-bombing attack it can be disruptive and confusing. If employees have education beforehand, they’ll be better prepared to defend themselves.
Let employees know what push-bombing is and how it works. Provide them with training on what to do if they receive MFA notifications they didn’t request.
You should also give your staff a way to report these attacks. This enables your IT security team to alert other users. They can then also take steps to secure everyone’s login credentials.
Need help enhancing your employee training? Contact Databranch today or visit us here to learn more about our Breach Prevention Platform and Security Awareness Training with simulated phishing tests.
Reduce Business App “Sprawl”
On average, employees use 36 different cloud-based services per day. That’s a lot of logins to keep up with. The more logins someone has to use, the greater the risk of a stolen password.
Take a look at how many applications your company uses. Look for ways to reduce app “sprawl” by consolidating. Platforms like Microsoft 365 and Google Workspace offer many tools behind one login. Streamlining your cloud environment improves security and productivity.
Adopt Phishing-Resistant MFA Solutions
You can thwart push-bombing attacks altogether by moving to a different form of MFA.
Phishing-resistant MFA uses a device passkey or physical security key for authentication.
There is no push notification to approve with this type of authentication. This solution is more complex to set up, but it’s also more secure than text or app-based MFA.
Visit our website here to learn more about passkeys along with the other 2 main forms of MFA.
Enforce Strong Password Policies
For hackers to send several push-notifications, they need to have the user’s login.
Enforcing strong password policies reduces the chance that a password will get breached.
Standard practices for strong password policies include:
- Using at least one upper and one lower-case letter
- Using a combination of letters, numbers, and symbols
- Not using personal information to create a password
- Storing passwords securely
- Not reusing passwords across several accounts
Put in Place an Advanced Identity Management Solution
Advanced identity management solutions can also help you prevent push-bombing attacks. They will typically combine all logins through a single sign-on solution. Users, then have just one login and MFA prompt to manage, rather than several.
Additionally, businesses can use identity management solutions to install contextual login policies. These enable a higher level of security by adding access enforcement flexibility.
The system could automatically block login attempts outside a desired geographic area. It could also block logins during certain times or when other contextual factors aren’t met.
Do You Need Help Improving Your Identity & Access Security?
Multi-factor authentication alone isn’t enough. Companies need several layers of protection to reduce their risk of a cloud breach.
Are you looking for some help to reinforce your cybersecurity? To learn more about how we can help take this off your IT plate, call 716-373-4467 x 115 or email [email protected].
Article used with permission from The Technology Press.
Read More

Once upon a time, our most precious assets were confidently protected behind layers of security defenses. Cash was neatly stacked in a cast metal safe which was bolted to the floor of the building. Customer lists and bank records were locked in a filing cabinet and only accessible to the person who had the key. Human Resource records were protected by the shelter of the impenetrable HR office door.
Then, digital electronics revolutionized the typical business office. Instead of accessing records from a locked filing cabinet, employees now used computers to navigate a digital file system which contained an abundance of information – much of it considered to be confidential. The sensitive documents that were once tangible and secured behind a physical lock and key were now accessible in digital format and stored in the data network for end users to access.
Security controls such as passwords and file permissions were established to protect the confidential information in its new digital format. This was a time however, when computing devices were stationary and did not typically leave the confines of the physical office. Employees would report to the office for work, log onto their computer, and only then – be granted with access to confidential information. The data that companies treasured most rarely – if ever – left the building.
The same statement cannot be made today. Mobile computing devices are very popular and can be found in most corporate computing devices. Employees are no longer forced to work on a computer that is tethered to the floor beneath their office desk. Laptops and tablets have provided employees with the freedom and flexibility to work from just about anywhere. Mobile devices have also changed the corresponding security landscape too.
The Customer Lists, HR records and Bank Statements are now leaving the building.
The 2 Significant Risks Associated with Mobile Computing Devices:
People lose them and people steal them.
The most common item stolen by thieves is cash, the second is electronic devices. So, what happens when the hotel maid swipes your work laptop or tablet? Or, what if it’s accidentally left at a train station or airport?
The answer to both questions is simple: Someone now has a device that contains sensitive and confidential business information. Chances are that “Someone” is not a trusted entity at all. Many data breaches start with a stolen work device. The stolen property is then compromised, and the thief has the ability to use or sell the stolen data.
There is no doubt that mobile computing devices pose a real security challenge. We have grown accustomed to the elasticity they provide and it is unreasonable to think we will revert back to using the stationary computer we once used at our desk. Laptops and tablets are here to stay.
Human beings will continue to lose these devices and criminals will continue to steal them. Although we can fight to minimize these occurrences through effective awareness training, the reality is that we will not be able to prevent them all together.
However, there are security controls you can put in place to help minimize your businesses risk when it comes to laptops and tablets.
Use a VPN
Free Wi-Fi may be a welcome site when you’re on the road, but it can also be dangerous. You don’t know who else is using that Wi-Fi. A hacker hanging out on the connection can easily steal your data if you’re not protected.
It’s better to use either your mobile carrier connection or a virtual private network (VPN) app. VPN plans are inexpensive and will keep your data encrypted, even if you’re on public Wi-Fi. It is highly recommended that VPNs are secured using Multi-Factor Authentication, this provides an additional layer of security against threat actors.
Visit our website here to learn more about VPNs and what factors to consider when choosing a plan.
Backup Your Data
Don’t lose all your work data with the device! Back up your devices to the cloud or local storage before you travel. This ensures that you won’t lose the valuable information on your device.
Need help with a Data Backup and Recovery plan for your business? Contact us today or visit our website to learn more.
Restrict Privileges
Local Admin Privileges allow employees to make adjustments to their work computers without the need for IT interference. This means that they can download programs, connect to printers, and modify software already installed on their computer.
This can be convenient, but poses a major cybersecurity risk.
If a device is stolen and the thief were to gain access to an account with local admin privileges, the damage could be endless. This is especially true for a business that is not utilizing security measures such as Multi-Factor Authentication (MFA) or Password Managers.
Once a hacker has breached your computer they could download malware, spyware, or even ransomware. Resulting in computer files being locked, credentials being stolen, or even a virus spreading throughout your entire network.
Visit our website here to learn more about Local Admin Privileges.
Databranch Can Help
There are key digital solutions we can put in place to keep your business safer from online threats. Contact us today at at 716-373-4467 x115 or [email protected] to schedule a chat about mobile security.
Content provided curtesy of Cyberstone.
Read More

The need to back up data has been around since floppy disks. Data loss happens due to viruses, hard drive crashes, and other mishaps. Most people using any type of technology have experienced data loss at least once.
There are about 140,000 hard drive crashes in the US weekly. Every five years, 20% of SMBs suffer data loss due to a major disaster. How would you business be effected if you lost most of your critical business data? Visit our website here to set your Recovery Time Objectives (RTO) and calculate your recovery cost.
This increate in data loss has helped to drive a robust cloud backup market that continues to grow.
But one thing that’s changed with data backup in the last few years is security. Simply backing up data so you don’t lose it, isn’t enough anymore. Backing up has morphed into data protection.
What does this mean?
It means that backups need more cybersecurity protection. They face threats such as sleeper ransomware and supply chain attacks. Cloud-based backup has the benefit of being convenient, accessible, and effective. But there is also a need for certain security considerations with an online service.
Companies need to consider data protection when planning a backup and recovery strategy. The security tools used nowadays have to protect against the growing number of threats.
Some of the modern threats to data backups include:
- Data Center Outage: The “cloud” basically means data on a server. That server is internet accessible. Those servers can crash. Data centers holding the servers can also have outages.
- Sleeper Ransomware: This type of ransomware stays silent after infecting a device. The goal is to have it infect all backups. Then, when it’s activated, the victim doesn’t have a clean backup to restore.
- Supply Chain Attacks: Supply chain attacks have been growing. They include attacks on cloud vendors that companies use. Those vendors suffer a cyberattack that then spreads throughout their clients.
- Misconfiguration: Misconfiguration of security settings can be a problem. It can allow attackers to gain access to cloud storage. Those attackers can then download and delete files as they like. Visit our website here to read more about the Misconfiguration of Cloud Applications.
What to Look for in a Data Protection Backup System
Just backing up data isn’t enough. You need to make sure the application you use provides adequate data protection. Here are some of the things to look for when reviewing a backup solution.
Ransomware Prevention
Ransomware can spread throughout a network to infect any data that exists. This includes data on computers, servers, and mobile devices. It also includes data in cloud platforms syncing with those devices.
95% of ransomware attacks also try to infect data backup systems.
It’s important that any data backup solution you use, has protection from ransomware. This type of feature restricts automated file changes that can happen to documents.
Continuous Data Protection
Continuous data protection is a feature that will back up files as users make changes. This differs from systems that back up on a schedule, such as once per day.
Continuous data protection ensures that the system captures the latest file changes. This mitigates data loss that can occur if a system crashes before the next backup. With the speed of data generation these days, losing a day’s worth of data can be very costly.
Threat Identification
Data protection incorporates proactive measures to protect files. Look for threat identification functions in a backup service. Threat identification is a type of malware and virus prevention tool.
It looks for malware in new and existing backups. This helps stop sleeper ransomware and similar malware from infecting all backups.
Zero-Trust Tactics
Cybersecurity professionals around the world promote zero-trust security measures. This includes measures such as multi-factor authentication and application safelisting.
A zero-trust approach holds that all users and applications need ongoing authentication. So, just because a user is logged into the system today, doesn’t mean they are completely trusted.
Some of the zero-trust features to look for include:
Backup Redundancy
If you back up to a USB drive or CD, you have one copy of those files. If something happens to that copy, you could experience data loss.
Cloud backup providers should have backup redundancy in place. This means that the server holding your data mirrors that data to another server. This prevents data loss in the case of a server crash, natural disaster, or cyberattack.
At Databranch, our Datto devices utilize a reliable data backup redundancy solution by storing your critical business data onto your local Datto device as well as 2 offsite cloud storages.
Air Gapping for More Sensitive Data
Air gapping is a system that keeps a copy of your data offline or separated in another way. This would entail making a second backup copy of your data. Then, putting it on another server that is disconnected from external sources.
This is a feature that you may want to seek out if you deal with highly sensitive data. It helps to ensure that you have at least one other copy of your backup. A copy walled off from common internet-based attacks.
Need Help With Secure Backup & Data Protection Solutions?
With Datto, your company can be up and running in just seconds after a disaster. Instant virtualization combined with the ability to backup as frequently as every 5 minutes means that with the click of a button, your Datto device recreates your computers and servers so your business can resume as if nothing had ever happened.
Our Datto devices utilize a reliable data backup redundancy solution by storing your critical business data onto your local Datto device as well as 2 offsite cloud storages. Datto even includes ransomware detection by running analytics to compare the two most recent backup snapshots to identify ransomware footprints.
Have you updated your backup process for today’s threats? Contact us today at 716-373-4467 x115 or [email protected] to schedule a chat about data backup and protection.
You can also visit our website to learn more about Datto and the benefits it provides.
Article used with permission from The Technology Press.
Read More
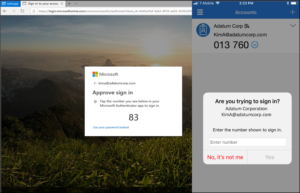
Upcoming Changes to Microsoft Office 365 Authenticator App
Microsoft has announced an upcoming change to the default method used in its Authenticator App. Starting May 8th, 2023, users will be required to input a verification number into the authenticator app. This date was previously February 27th, but Microsoft recently released a revision to the start date.
This number matching method is replacing the approve/deny push notification sent to mobile devices. Number matching is a key security upgrade to traditional second factor notifications in Microsoft Authenticator.
Microsoft will remove the admin controls and enforce the number match experience tenant-wide for all users starting May 8th, 2023.
Please note that this change will occur for both PCs and mobile devices. No action is required by the end users, this change will happen automatically by Microsoft.
If you have any questions regarding this upcoming change, or need any assistance, please contact Databranch Service at 716-373-4467 x4.
Microsoft Office 365 Changes to Security Defaults
Security Defaults are the preconfigured security settings that exist on your Microsoft accounts. Microsoft has announced that throughout the spring and summer of 2023, they will be rolling out Azure AD Security Defaults to all existing tenants.
Some of the changes enforced by the Security Defaults are below:
- Requiring all users and admins to register for MFA using the Microsoft Authenticator app.
- Challenging users with MFA, mostly when they show up on a new device or app, but more often for critical roles and tasks.
- Disabling authentication from legacy authentication clients that can’t do MFA.
- Protecting admins by requiring extra authentication every time they sign in.
Things to watch for:
- Automated emails/Reports from applications and vendors
- Scan to File Share
- Email functionality from applications
Customers will have the ability to disable the settings or configure alternate conditional access policies. However, disabling the Security Defaults would create vulnerabilities across your Microsoft accounts leaving your organization’s cybersecurity at risk.
Microsoft released Security Defaults back in 2019 to ensure that basic cybersecurity measures, such as MFA, were being used on their accounts. Because of this, over 30 million organizations already have baseline Security Defaults in place. This has allowed these companies to experience 80% less compromised accounts compared to companies without Security Defaults.
MFA alone is known for being the most effective tool at preventing compromised accounts, yet it is one of the most underutilized security measures. Microsoft’s Security Report states that MFA can block over 99.9% of account compromised attacks.
Databranch has taken the step of proactively enabling these Security Defaults for our own Microsoft tenant. This not only improves the cybersecurity of our Microsoft accounts, but it will also allow us to experience these changes first hand so we can better serve our clients.
We are also performing a review of the Office 365 tenants for all of our managed clients, so that we can proactively get their Security Defaults enabled, if they are not already.
Reach out today at [email protected] or 716-373-4467 if you have questions about these changes or wish to speak with one of our team members about enabling MFA for more accounts.
Read More

Our technology inevitably comes with us when we travel. Some people won’t even travel to the end of the block without their smartphones. Whether you travel for work or pleasure, not having your technology there when you need it can ruin your day.
Travel smarter and more securely by doing several checks before you go. Use our handy tech travel checklist below, it can save you from lost devices or a data breach.
1. Check Your Apps
Have you ever sat at an airport gate wondering why it looked so empty? You then found out that your gate had changed, and you had no idea. You go rushing to the other end of the concourse, hoping you’re not too late.
How did everyone else know about the gate change? They most likely had the app for the airline and received a notification.
Before you leave for a trip, make sure to download any apps you may need. It’s better to download them when you’re at home on your own Wi-Fi. Waiting until you’re at the airport could cause connectivity or security issues.
Some of the apps you may want to download or update before your trip are:
- Airline app
- Train app
- Hotel app
- Weather app
- City tourism app
2. Check Your Cords & Adapters
People leave behind countless chargers and adapters every day. They litter airports, restaurants, and train stations around the world. Make sure to bring a backup charger for your laptop, tablet, or phone. Otherwise, you may find yourself paying a premium price for a new charger in a gift shop.
3. Check Your Power
A great way to ensure you have the power you need is to buy a small portable battery. You can find these in most major retailers or online. They are small “blocks” that hold a charge and can power up a cell phone in a pinch.
Having this extra backup also helps you avoid potential juice-jacking ports. These are fake or compromised public USB charging ports that hackers use them to steal your data when you plug in your device.
4. Check Your Mobile Plan
Traveling for work is exciting, but it can also lead to issues connecting with clients. Being away from the office means missed calls an unheard voicemails.
Handing out you personal mobile number may seem like a good solution. However, having clients or coworkers reach you at all hours of the day can blur the line between your professional and personal life. It can also get expensive if you’re on long calls or using your own mobile data.
An alternative is to set up a VoIP app that you can use with your office while you’re traveling. These enable both calls and SMS, but you do need an internet connection.
Interested in learning more about VoIP and the functions it provides? Reach out to Databranch today! Our Rock-It VoIP platform offers flexibility and scalability to accommodate for fluctuations and growth in your business, and we can service locations nationwide. With Rock-IT VoIP, we also port your numbers so they stay the same and handle any upgrades, maintenance, and programming!
5. Check or Add a VPN
Free Wi-Fi may be a welcome site when you’re on the road, but it can also be dangerous. You don’t know who else is using that Wi-Fi. A hacker hanging out on the connection can easily steal your data if you’re not protected.
It’s better to use either your mobile carrier connection or a virtual private network (VPN) app. VPN plans are inexpensive and will keep your data encrypted, even if you’re on public Wi-Fi.
Visit our website here to learn more about VPNs and what factors to consider when choosing a plan.
6. Check Your Backup
Unfortunately, mishaps occur when traveling. You may leave your phone behind in the airport, have your luggage lost, or get your device stolen while in a crowded area.
10% of all laptop thefts happen in airports.
Don’t lose all your work data with the device! Back up your devices to the cloud or local storage before you travel. This ensures that you won’t lose the valuable information on your device.
Need help with a Data Backup and Recovery plan for your business? Contact us today or visit our website to learn more.
7. Check Your Device Security
Make your devices as secure as possible before you hit the road. When we’re traveling, our minds are occupied by other things. So, you may not think to check your antivirus or avoid suspicious phishing links.
Protect your devices before you go using:
- Antivirus/anti-malware
- DNS filtering
- Screen lock with passcode
- Sharing features turned off
- VPN application
- Find-My-Device feature turned on
Improve the Security of Your Devices Now
Don’t leave your company devices unprotected. Contact us today if you want to discuss your cybersecurity in greater detail. We can arrange a quick chat to discussed some options we have available that would help enhance your businesses security. Give us a call at 716-373-4467 x 115 or email us at [email protected] to learn more.
Article used with permission from The Technology Press.
Read More

Phishing. It seems you can’t read an article on cybersecurity without it coming up. That’s because phishing is still the number one delivery vehicle for cyberattacks.
A cybercriminal may want to steal employee login credentials, launch a ransomware attack, or possibly plant spyware to steal sensitive info. For a hacker, sending a phishing email can accomplish all of this.
80% of surveyed security professionals say that phishing campaigns have significantly increased post-pandemic.
Phishing not only continues to work, but it’s also increasing in volume due to the increase in remote workers. Many employees are now working from home and don’t have the same network protections they had when working at the office.
Why has phishing continued to work so well after all these years? Aren’t people finally learning what phishing looks like?
It’s true that people are generally more aware of phishing emails and have gotten better at stopping them. However, it’s also true that these emails are becoming harder to recognize as scammers evolve their tactics.
One of the newest tactics is particularly hard to detect, the reply-chain phishing attack.
What is a Reply-Chain Phishing Attack?
Just about everyone is familiar with reply chains in email. An email is sent to one or more people, one replies, and that reply sits at the bottom of the new message. Then another person chimes in on the conversation, replying to the same email.
Soon, you have a chain of email replies on a particular topic. It lists each reply one under the other so everyone can follow the conversation.
You don’t expect a phishing email tucked inside that ongoing email conversation. Most people are expecting phishing to come in as a new message, not a message included in an ongoing reply chain.
The reply-chain phishing attack is particularly insidious because it does exactly that. It inserts a convincing phishing email in the ongoing thread of an email reply chain.
How Does a Hacker Gain Access to the Reply Chain?
How does a hacker gain access to the reply chain conversation? By hacking the email account of one of those people copied on the email chain.
The hacker can email from an email address that the other recipients recognize and trust. They also gain the benefit of reading down through the chain of replies. This enables them to craft a response that looks like it fits.
For example, they may see that everyone has been weighing in on a new product idea. So, they send a reply that says, “I’ve drafted up some thoughts on the new product, here’s a link to see them.”
The link will go to a malicious phishing site. The site might infect a visitor’s system with malware or present a form to steal more login credentials.
The reply won’t seem like a phishing email at all. It will be convincing because:
- It comes from an email address of a colleague. This address has already been participating in the email conversation.
- It may sound natural and reference items in the discussion.
- It may use personalization. The email can call others by the names the hacker has seen in the reply chain.
Business Email Compromise is Increasing
Business email compromise (BEC) is so common that it now has its own acronym. Weak and unsecured passwords lead to email breaches. So do data breaches that reveal databases full of user logins. Both are contributors to how common BEC is becoming.
In 2021, 77% of organizations saw business email compromise attacks. This is up 65% compared to the year before.
Credential theft has become the main cause of data breaches globally.
The reply-chain phishing attack is one of the ways that hackers turn that BEC into money. They either use it to plant ransomware or other malware or to steal sensitive data to sell on the Dark Web.
Tips for Addressing Reply-Chain Phishing
Here are some ways that you can lessen the risk of reply-chain phishing in your organization:
- Use a Business Password Manager: This reduces the risk that employees will reuse passwords across many apps. It also keeps them from using weak passwords since they won’t need to remember them anymore. Click here to learn more about our password manager solution, LastPass.
- Put Multi-Factor Controls on Email Accounts: Present a system challenge (question or required code). Using this for email logins from a strange IP address can stop account compromise. You can learn more about MFA here.
- Teach Employees to be Aware: Awareness is a big part of catching anything that might be slightly “off” in an email reply. Many attackers do make mistakes. Our Security Awareness Training will give your employees the tools they need to identify threats. Click here to learn more.
How Strong Are Your Email Account Protections?
Do you have enough protection in place on your business email accounts to prevent a breach? Let us know if you’d like some help!
Databranch has a foundation security suite with systems in place to identify any anomalies before cyber criminals have a chance to do significant damage to your network. Contact us at 716-373-4467 x 15, [email protected], or request more information below.
Article used with permission from The Technology Press.
Read More

Stolen login credentials are a hot commodity on the Dark Web. There’s a price for every type of account from online banking to social media. For example, hacked social media accounts will go for between $30 to $80 each.
The rise in reliance on cloud services has caused a big increase in breached cloud accounts. Compromised login credentials are now the #1 cause of data breaches globally, according to IBM Security’s latest Cost of a Data Breach Report.
Having either a personal or business cloud account compromised can be very costly. It can lead to a ransomware infection, compliance breach, identity theft, and more.
To make matters more challenging, users are still adopting bad password habits that make it all too easy for criminals. For example:
- 34% of people admit to sharing passwords with colleagues
- 44% of people reuse passwords across work and personal accounts
- 49% of people store passwords in unprotected plain text documents
Cloud accounts are more at risk of a breach than ever, but there are several things you can do to reduce the chance of having your online accounts compromised.
Use Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is the best method there is to protect cloud accounts. While not a failsafe, it is proven to prevent approximately 99.9% of fraudulent sign-in attempts, according to a study cited by Microsoft.
When you add the second requirement to a login, which is generally to input a code that is sent to your phone, you significantly increase account security. In most cases, a hacker is not going to have access to your phone or another device that receives the MFA code, thus they won’t be able to get past this step.
The brief inconvenience of using that additional step when you log into your accounts is more than worth it for the bump in security.
Use a Password Manager for Secure Storage
One way that criminals get their hands on user passwords easily is when users store them in unsecured ways. Such as in an unprotected Word or Excel document or the contact application on their PC or phone.
Using a password manager provides you with a convenient place to store all your passwords that is also encrypted and secured. Plus, you only need to remember one strong master password to access all the others.
Password managers can also autofill all your passwords in many different types of browsers, making it a convenient way to access your passwords securely across devices.
Review/Adjust Privacy & Security Setting
Have you taken time to look at the security settings in your cloud tools? One of the common causes of cloud account breaches is misconfiguration. This is when security settings are not properly set to protect an account.
You don’t want to just leave SaaS security settings at defaults, as these may not be protective enough. Review and adjust cloud application security settings to ensure your account is properly safeguarded.
Use Leaked Password Alerts in Your Browser
You can have impeccable password security on your end, yet still have your passwords compromised. This can happen when a retailer or cloud service you use has their master database of usernames and passwords exposed and the data stolen.
When this happens, those leaked passwords can quickly end up for sale on the Dark Web without you even knowing it.
Due to this being such a prevalent problem, browsers like Chrome and Edge have had leaked password alert capabilities added. Any passwords that you save in the browser will be monitored, and if found to be leaked, you’ll see an alert when you use it.
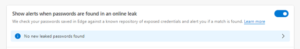
Look for this in the password area of your browser, as you may have to enable it. This can help you know as soon as possible about a leaked password, so you can change it.
Don’t Enter Passwords When on a Public Wi-Fi
Whenever you’re on public Wi-Fi, you should assume that your traffic is being monitored. Hackers like to hang out on public hot spots in airports, restaurants, coffee shops, and other places so they can gather sensitive data, such as login passwords.
You should never enter a password, credit card number, or other sensitive information when you are connected to public Wi-Fi. You should either switch off Wi-Fi and use your phone’s wireless carrier connection or use a virtual private network (VPN) app, which encrypts the connection.
Use Good Device Security
If an attacker manages to breach your device using malware, they can often breach your accounts without a password needed. Just think about how many apps on your devices you can open and already be logged in to.
To prevent an online account breach that happens through one of your devices, make sure you have strong device security. Best practices include:
- Antivirus/anti-malware
- Up-to-date software and OS
- Phishing protection (like email filtering and DNS filtering)
Looking for Password & Cloud Account Security Solutions?
Don’t leave your online accounts at risk. We can help you review your current cloud account security and provide helpful recommendations. Contact Databranch today at 716-373-4467 x 15 or [email protected] if you would like to enhance your security and want to discuss you options.
Article used with permission from The Technology Press.
Read More



















