
Buyer beware – software programs or tools that claim the ability to conduct a risk assessment by scanning your network with little to no human interaction should raise concern!
These tools will generally do a nice job discovering vulnerabilities that exist in your technology environment, but vulnerabilities are not risks by default.
Is you business familiar with vulnerability assessments and their benefits? If not, visit our website here to learn more about the benefits and how they can enhance your cybersecurity posture.
What is Needed
Risk requires the presence of a vulnerability PLUS the action of threat actor.
To illustrate this concept using an example from the tangible world, lets visualize a car. The car is parked, and the doors are unlocked. A premature conclusion would be to state that the doors being unlocked translates to risk. If you apply critical thought however, you will discover that the unlocked doors are simply a vulnerability that could be exploited.
You would need more information to determine actual risk. Is there anything valuable in the car? What is the crime rate associated with the place the car is parked? What would the impact be if someone gained access to the car? Who would attempt to gain access to the car? Are there other compensating controls in place, like a security camera? The same logic applies to the digital world.
The presence of vulnerabilities like unpatched computers or misconfigured devices will contribute to the likelihood of a risk event occurring, but it is shortsighted to say that vulnerabilities equal risk. That statement simply is not true.
A risk assessment requires critical thought to occur beyond the discovery of vulnerabilities by software tools. It requires critical thinking and the use of logic and reason. All of which made capable by the involvement of qualified human beings during the risk assessment process.
Relying on the arbitrary risk statements and scores created by software tools that simply discover vulnerabilities in your network, can lead to a false understanding of your actual risk profile. This can then easily lead to the wasteful allocations of resources – intended to reduce risk – but end up remediating a vulnerability instead.
What Happens After the Assessment?
Typically, a vulnerability assessment can be completed in a day or two. The results of a vulnerability assessment are documented and provided to the stakeholder complete with recommendations around remediating any weaknesses found.
Security shortcomings found during a vulnerability assessment can almost always be fixed. Many times, the fixes are very easy to accomplish. Roughly 60% of all reported cybersecurity breaches occurred because the bad actors exploited common vulnerabilities and exposures (CVE).
This means that roughly 60% of all reported cybersecurity breaches could have been prevented if the victim had simply conducted a vulnerability assessment and made small improvements to their cybersecurity posture that would have eliminated a substantial amount of risk.
Interested in setting up a vulnerability assessment? Contact Databranch today at 716-373-4467 x115, [email protected] , or fill in the form below to set up a meeting with one of our experienced team members.
Not only will we help with the assessment, but our team of highly trained engineers will help your business prioritize based on your specific business needs.
Content was provided courtesy of CyberStone.
Read More

What does “End of Support” mean? It means that after this date, these products will no longer receive non-security updates, security updates, bug fixes, or technical support. It also means that you will not be in compliance with most industry wide compliance standards and regulations.
What Should I Be Doing?
- Start planning your migration NOW.
- Determine how many instances of Server 2012(R2) are being utilized in your current network setup.
- Assess the upgrade path for applications that currently run on these operating systems.
- Allocate resources and budget for necessary hardware upgrades to transition to a newer version.
What Happens If I Don’t Upgrade?
Security & Compliance Issues
Software and OS vulnerabilities are sought out and exploited all the time. This is what hackers do for a living. The vulnerability cycle usually begins with hackers finding a software “loophole.” They then write code to exploit it that allows them some type of system access.
The software developer learns of this, usually once hackers start breaching systems. They write code to fix that vulnerability. Developers then send the fix to users via an update that they install. This protects the device from one or more hacker exploits.
When a software reaches its end of life, these fixes are no longer made. The developer has moved on to focus on its newer products. So, the vulnerability remains. It leaves a device vulnerable to hacks for days, months, or years afterward.
Approximately 61% of security vulnerabilities in corporate networks are over five years old.
Visit us here to learn more about penetration testing and how it helps identify the vulnerabilities in your business.
If you have to comply with a data privacy regulation, like HIPAA, you’ll also run into issues. Data privacy rules dictate making reasonable efforts to protect data. Using a device with a outdated software jeopardizes meeting compliance.
Slowed Productivity
The older a system gets, the slower it will get. Staff that must work on outdated software often complain that it hurts productivity. 77% of surveyed employees were frustrated with outdated tech. Employees dealing with outmoded systems may also quit. They are 450% more likely to want to leave and work elsewhere.
An outdated operating system can hold your staff back. They will miss out on modern time-saving features and they can also run into problems with bugs that will no longer get fixed.
Incompatibility With Newer Tools
Software and hardware developers aren’t looking back. Once Windows Server 2012 reaches “End of Life”, they aren’t prioritizing its compatibility. In fact, some may not want their product to be compatible with it because of the liability.
When you run into issues because of outdated software and modern hardware, it hurts your business. You become less competitive and begin to fall behind.
Get Help With Your Windows Upgrades
The good news is, we are still six months away from the end of support date. But it’s important to start preparing now. Databranch has successfully migrated numerous clients and our team is excited to work with you to create a migration plan for your organization! Reach out today at 716-373-4467 x115 or [email protected] to speak with one of our experienced team members.
Read More

Companies both large and small share this one cybersecurity problem. They have computers that are still running older operating systems. Staff might use these devices only occasionally or the company may be running customized software that won’t run on newer OS versions.
The problem is that when the OS becomes outdated, the system is open to cyberattacks. When Microsoft or another developer retires an OS, it means that it is no longer supported. No more feature updates and no more security patches for newly found vulnerabilities.
The latest operating system to lose all support is Windows 8.1. Microsoft released the OS in 2013, and it was officially retired on January 10, 2023. Microsoft issued the following warning for companies:
“Continuing to use Windows 8.1 after January 10, 2023 may increase an organization’s exposure to security risks or impact its ability to meet compliance obligations.”
Here are a few facts you should know about what this retirement of Windows 8.1 means.
The OS Will Still Technically Work
When an operating system reaches its end of life, it doesn’t just stop working. Thus, many companies go on using it without realizing the security risk. Technically, the OS will work as it did the day before retirement. But it’s a lot less safe due to the loss of support.
Your System Will No Longer Receive Security Patches
Software and OS vulnerabilities are sought out and exploited all the time. This is what hackers do for a living. The vulnerability cycle usually begins with hackers finding a software “loophole.” They then write code to exploit it that allows them some type of system access.
The software developer learns of this, usually once hackers start breaching systems. They write code to fix that vulnerability. Developers then send the fix to users via an update that they install. This protects the device from one or more hacker exploits.
When an OS reaches its end of life, these fixes are no longer made. The developer has moved on to focus on its newer products. So, the vulnerability remains. It leaves a device vulnerable to hacks for days, months, or years afterward.
Approximately 61% of security vulnerabilities in corporate networks are over five years old.
Visit us here to learn more about penetration testing and how it helps identify the vulnerabilities in your business.
Options for Upgrading
If you have a computer that is still running Windows 8.1, you have two options for upgrading. You can opt for Windows 10 or Windows 11. If the computer is running such an old OS, there is a chance your system may not meet the requirements for one or both. In this case, you may need to buy a new device altogether.
Microsoft states that there is no free option to upgrade from 8.1 to Windows 10 or 11. Some of the advantages you gain when upgrading include:
- Better built-in security
- Faster processing
- Capability for more modern features (like facial recognition)
- Improved accessibility features
- Updated productivity tools (like snap layouts in Windows 11)
What Happens If I Don’t Upgrade?
Security & Compliance Issues
Your data security is at risk if you stay on Windows 8.1. Without any security updates, any vulnerabilities will stay unpatched. This leaves your system highly vulnerable to a breach. One hacked system on a network can also cause the breach or malware infection to spread to newer devices.
If you have to comply with a data privacy regulation, like HIPAA, you’ll also run into issues. Data privacy rules dictate making reasonable efforts to protect data. Using a device with an outdated OS jeopardizes meeting compliance.
Slowed Productivity
The older a system gets, the slower it will get. Staff that must work on outdated software often complain that it hurts productivity. 77% of surveyed employees were frustrated with outdated tech. Employees dealing with outmoded systems may also quit. They are 450% more likely to want to leave and work elsewhere.
An outdated operating system can hold your staff back. They miss out on modern time-saving features. They can also run into problems with bugs that will no longer get fixed.
Incompatibility With Newer Tools
Software and hardware developers aren’t looking back. Once Microsoft retires an OS, they aren’t prioritizing its compatibility. In fact, some may not want their product to be compatible with it because of the liability.
When you have issues using modern software and hardware it hurts your business. You become less competitive and begin to fall behind. Staying on an outmoded OS keeps you stuck in the past.
Get Help With Your Windows Upgrades
All Databranch Comprehensive Care and Foundation Security clients have scheduled automatic patching and Windows updates on their devices. To learn more about how we can help take this off your IT plate or help your organization upgrade to a system with a supported operating system, call 716-373-4467 x 115, email [email protected] or visit us here to learn more.
Article used with permission from The Technology Press.
Read More

The need to back up data has been around since floppy disks. Data loss happens due to viruses, hard drive crashes, and other mishaps. Most people using any type of technology have experienced data loss at least once.
There are about 140,000 hard drive crashes in the US weekly. Every five years, 20% of SMBs suffer data loss due to a major disaster. How would you business be effected if you lost most of your critical business data? Visit our website here to set your Recovery Time Objectives (RTO) and calculate your recovery cost.
This increate in data loss has helped to drive a robust cloud backup market that continues to grow.
But one thing that’s changed with data backup in the last few years is security. Simply backing up data so you don’t lose it, isn’t enough anymore. Backing up has morphed into data protection.
What does this mean?
It means that backups need more cybersecurity protection. They face threats such as sleeper ransomware and supply chain attacks. Cloud-based backup has the benefit of being convenient, accessible, and effective. But there is also a need for certain security considerations with an online service.
Companies need to consider data protection when planning a backup and recovery strategy. The security tools used nowadays have to protect against the growing number of threats.
Some of the modern threats to data backups include:
- Data Center Outage: The “cloud” basically means data on a server. That server is internet accessible. Those servers can crash. Data centers holding the servers can also have outages.
- Sleeper Ransomware: This type of ransomware stays silent after infecting a device. The goal is to have it infect all backups. Then, when it’s activated, the victim doesn’t have a clean backup to restore.
- Supply Chain Attacks: Supply chain attacks have been growing. They include attacks on cloud vendors that companies use. Those vendors suffer a cyberattack that then spreads throughout their clients.
- Misconfiguration: Misconfiguration of security settings can be a problem. It can allow attackers to gain access to cloud storage. Those attackers can then download and delete files as they like. Visit our website here to read more about the Misconfiguration of Cloud Applications.
What to Look for in a Data Protection Backup System
Just backing up data isn’t enough. You need to make sure the application you use provides adequate data protection. Here are some of the things to look for when reviewing a backup solution.
Ransomware Prevention
Ransomware can spread throughout a network to infect any data that exists. This includes data on computers, servers, and mobile devices. It also includes data in cloud platforms syncing with those devices.
95% of ransomware attacks also try to infect data backup systems.
It’s important that any data backup solution you use, has protection from ransomware. This type of feature restricts automated file changes that can happen to documents.
Continuous Data Protection
Continuous data protection is a feature that will back up files as users make changes. This differs from systems that back up on a schedule, such as once per day.
Continuous data protection ensures that the system captures the latest file changes. This mitigates data loss that can occur if a system crashes before the next backup. With the speed of data generation these days, losing a day’s worth of data can be very costly.
Threat Identification
Data protection incorporates proactive measures to protect files. Look for threat identification functions in a backup service. Threat identification is a type of malware and virus prevention tool.
It looks for malware in new and existing backups. This helps stop sleeper ransomware and similar malware from infecting all backups.
Zero-Trust Tactics
Cybersecurity professionals around the world promote zero-trust security measures. This includes measures such as multi-factor authentication and application safelisting.
A zero-trust approach holds that all users and applications need ongoing authentication. So, just because a user is logged into the system today, doesn’t mean they are completely trusted.
Some of the zero-trust features to look for include:
Backup Redundancy
If you back up to a USB drive or CD, you have one copy of those files. If something happens to that copy, you could experience data loss.
Cloud backup providers should have backup redundancy in place. This means that the server holding your data mirrors that data to another server. This prevents data loss in the case of a server crash, natural disaster, or cyberattack.
At Databranch, our Datto devices utilize a reliable data backup redundancy solution by storing your critical business data onto your local Datto device as well as 2 offsite cloud storages.
Air Gapping for More Sensitive Data
Air gapping is a system that keeps a copy of your data offline or separated in another way. This would entail making a second backup copy of your data. Then, putting it on another server that is disconnected from external sources.
This is a feature that you may want to seek out if you deal with highly sensitive data. It helps to ensure that you have at least one other copy of your backup. A copy walled off from common internet-based attacks.
Need Help With Secure Backup & Data Protection Solutions?
With Datto, your company can be up and running in just seconds after a disaster. Instant virtualization combined with the ability to backup as frequently as every 5 minutes means that with the click of a button, your Datto device recreates your computers and servers so your business can resume as if nothing had ever happened.
Our Datto devices utilize a reliable data backup redundancy solution by storing your critical business data onto your local Datto device as well as 2 offsite cloud storages. Datto even includes ransomware detection by running analytics to compare the two most recent backup snapshots to identify ransomware footprints.
Have you updated your backup process for today’s threats? Contact us today at 716-373-4467 x115 or [email protected] to schedule a chat about data backup and protection.
You can also visit our website to learn more about Datto and the benefits it provides.
Article used with permission from The Technology Press.
Read More

Technology vulnerabilities are an unfortunate side effect of innovation. When software companies push new updates, there are often weaknesses in the code. Hackers exploit these weaknesses until software makers address the vulnerabilities with a security patch. The cycle continues with each new software or hardware update.
It’s estimated that about 93% of corporate networks are susceptible to hacker penetration. Assessing and managing these network weaknesses isn’t always a priority for organizations. Many suffer breaches because of poor vulnerability management.
61% of security vulnerabilities in corporate networks are over 5 years old.
Many types of attacks take advantage of unpatched vulnerabilities in software code. This includes ransomware attacks, account takeover, and other common cyberattacks.
Whenever you see the term “exploit” when reading about a data breach, that’s an exploit of a vulnerability. Hackers write malicious code to take advantage of these “loopholes.” That code can allow them to elevate privileges, run system commands or perform other dangerous network intrusions.
Putting together an effective vulnerability management process can reduce your risk. It doesn’t have to be complicated. Just follow the steps we’ve outlined below to get started.
Vulnerability Management Process
Step 1. Identify Your Assets
First, you need to identify all the devices and software that you will need to assess. You’ll want to include all devices that connect to your network, including:
- Computers
- Smartphones
- Tablets
- IoT devices
- Servers
- Cloud services
Vulnerabilities can appear in many places. Such as the code for an operating system, a cloud platform, software, or firmware. So, you’ll want a full inventory of all systems and endpoints in your network.
This is an important first step, so you will know what you need to include in the scope of your assessment.
Step 2: Perform a Vulnerability Assessment
Next will be performing a vulnerability assessment. This is usually done by an IT professional, such as Databranch, using assessment software. This could also include penetration testing.
During the assessment, the professional scans your systems for any known vulnerabilities. The assessment tool matches found software versions against vulnerability databases.
For example, a database may note that a version of Microsoft Exchange has a vulnerability. If it detects that you have a server running that same version, it will note it as a found weakness in your security.
Learn more about the benefits of penetration testing here.
Step 3: Prioritize Vulnerabilities by Threat Level
The assessment results provide a roadmap for mitigating network vulnerabilities. There will usually be several, and not all are as severe as others. Next, you will need to rank which ones to address first.
At the top of the list should be the ones that experts consider severe. Many vulnerability assessment tools will use the Common Vulnerability Scoring System (CVSS). This categorizes vulnerabilities with a rating score from low to critical severity.
You’ll also want to rank vulnerabilities by your own business needs. If a software is only used occasionally on one device, you may consider it a lower priority to address. While a vulnerability in software used on all employee devices, you may rank as a high priority.
Step 4: Remediate Vulnerabilities
Remediate vulnerabilities according to the prioritized list. Remediation often means applying an issued update or security patch. But it may also mean upgrading hardware that may be too old for you to update.
Another form of remediation may be ringfencing. This is when you “wall off” an application or device from others in the network. A company may do this if a scan turns up a vulnerability for which a patch does not yet exist.
Increasing advanced threat protection settings in your network can also help. Once you’ve remediated the weaknesses, you should confirm the fixes.
Here at Databranch, our Managed Service plans offer proactive monitoring tools that helps us detect threats before they can impact your network. They also provide increased protection from malware, ransomware, and phishing compromises. Read more about the benefits of Managed Services here.
Step 5: Document Activities
It’s important to document the vulnerability assessment and management process. This is vital both for cybersecurity needs and compliance.
You’ll want to document when you performed the last vulnerability assessment. Then document all the steps taken to remediate each vulnerability. Keeping these logs will be vital in the case of a future breach. They also can inform the next vulnerability assessment.
Step 6. Schedule Your Next Vulnerability Assessment Scan
Once you go through a round of vulnerability assessment and mitigation, you’re not done. Vulnerability management is an ongoing process.
In 2022, there were over 22,500 new vulnerabilities documented. Developers continue to update their software continuously. Each of those updates can introduce new vulnerabilities into your network.
It’s a best practice to have a schedule for regular vulnerability assessments. The cycle of assessment, prioritization, mitigation, and documentation should be ongoing. This fortifies your network against cyberattacks. It removes one of the main enablers of hackers.
Get Started with a Vulnerability Assessment
Take the first step towards effective vulnerability management. We can help you fortify your network against attacks. Contact us today at 716-373-4467 x 115 or [email protected] to schedule a vulnerability assessment to get started. You can also fill out the form below to request your free baseline security assessment.
Article used with permission from The Technology Press.
Read More

Do you think paying monthly for IT support is unnecessary? Or does your staff just handle their own device security?
When a system goes down, then you can call someone to help… right?
Running a business without an IT support partner is like going through life with no regular doctor or auto mechanic.
Yeah, you can get by. You can get help in an emergency. But being reactive with your business operations could hurt your bottom line.
Managed IT support can lower your overall technology costs while also providing less downtime since employees aren’t interrupted all the time by computer problems. This means your team can focus on your customers instead of getting the Wi-Fi back up.
What do you get when you sign on for managed IT services?
- Ongoing management of your technology
- Fast response from someone that knows your business
- Proactive maintenance to ward off breakdowns
- Network security monitoring and attack prevention
- Tools that help you stay safe and efficient
- A full IT team vs. a single IT resource
- Databranch’s vCIO services for strategic technology planning & Technology Roadmap/Budget Creation
Here at Databranch, our Managed Network Services provides your company with the security of knowing that your network is being monitored and maintained on a 24/7 basis.
It’s designed to keep your network functioning seamlessly by utilizing a suite of cost-effective computer managed services that proactively monitor and support your network and Technology infrastructure.
Imagine a secured network with maximized uptime, predictable expenses, and optimized business availability – leaving you and your employees free to focus on what you do best: running your business.
See how much better your business can operate when a pro is handling your tech.
Questions about costs and services? Contact Databranch today at 716-373-4467 x 115, [email protected], or visit us here to schedule a chat.
Read More

March 31st is World Backup Day, an annual date celebrated by the tech industry to highlight the importance of protecting your data and keeping your systems secure. Yet, many businesses don’t have backup and recovery solutions in place for their critical business data.
It is common for organizations to invest in preventative cybersecurity defenses. In fact, most organizations have technologies such as firewalls and anti-virus software that are designed to stop a cyber-attack.
These controls certainly serve a purpose in fighting the war against cybercrime and should not be discounted but the reality is, defending your business from cyber-attacks is an incredibly hard task to do.
Hackers are anonymous, perimeters are not physical, attacks are sophisticated, and the volume of cyber assaults launched every day is astounding. Defending cyber-attacks is a little like entering a cage fight blindfolded with one arm tied behind your back.
Despite the best defensive efforts, you will get hit.
If you do not regularly backup critical data and systems, then you must start doing so immediately.
With Datto, your company can be up and running in just seconds after a disaster.
Instant virtualization combined with the ability to backup as frequently as every 5 minutes means that with the click of a button, your Datto device recreates your computers and servers so your business can resume as if nothing had ever happened.
Our Datto devices utilize a reliable data backup redundancy solution by storing your critical business data onto your local Datto device as well as 2 offsite cloud storages. Datto even includes ransomware detection by running analytics to compare the two most recent backup snapshots to identify ransomware footprints.
Have you updated your backup process for today’s threats? Contact us today at 716-373-4467 x115 or [email protected] to schedule a chat about data backup and protection.
You can also visit our website here to learn more about our data backup and recovery solutions.
Read More

There are many things that have changed since the invention of the internet. One of these is how we bank and access our accounts. You used to have to go into a local bank branch to make deposits and withdrawals. Now, you can take a picture of a check and deposit it from your phone.
Approximately 73% of people around the world use some form of online banking at least once a month. People have never had such convenient account access. But that convenience can come at a cost.
In 2021, account takeover fraud increased by 90%. New account fraud jumped a whopping 109%. As the ease of online banking has increased, so has banking-related cybercrime.
If someone breaches your Facebook account, it can be a real pain. But, if a hacker breaches your bank account, it can be devastating. It can mean significant losses. Losses that you may not be able to recoup from your financial institution.
In this article, we’ll take a look at the mistakes people make that leave their accounts at risk. Then, we’ll go over some important tips on how to keep your bank account better protected.
Mistakes That Allow Criminals to Access Your Account
Not Enabling Two-factor Authentication
Two-factor authentication (2FA) is a simple process that packs a big punch. When you enable this setting in an online account, it requires an extra step to gain access. That step usually consists of receiving a one-time passcode (OTP) by SMS and entering that at login.
Many people make the mistake of leaving this disabled. They either don’t know it’s there or they think it’s too inconvenient. But leaving this setting off makes it much easier for a bad actor to breach your account.
If you’ve ever had a company inform you that it’s had a data breach, it’s likely your details could be floating around the dark web. If that’s the case, it’s only a matter of time until you’re targeted by cyber criminals. Reach out to us today to learn more about our Dark Web monitoring services.
Falling for a Phishing Scam
There are several types of phishing scams that target online banking. Cyber criminals send emails that look like they come from your bank. They’ll even promise incredibly low rates on credit cards.
Other scams can involve warning you of unauthorized account activity. But when you click the link to log in, you’re actually on a fake page. One designed to look just like your normal bank website.
These are just a few ways that scammers can get your online banking login details. Once they have them, they’ll act immediately to get whatever they can.
Using Easy-to-Guess Passwords
If your account password is easy to remember, it’s also often easy to guess. Using weak passwords is a common mistake that enables many cyber criminals.
Some best practices for passwords include:
- Make them at least 10 characters long
- Include at least one number
- Include at least one symbol
- Include at least one upper-case letter
- Don’t make them personal (e.g., don’t use your birthdate, etc.)
Downloading Unsafe Mobile Apps
Banking trojans are often hidden in malicious mobile apps. These apps can look like something as innocent as a task manager. But, once installed, banking trojans seek out any details they can find. They are looking for banking and wallet apps.
Logging Into Online Banking While on Public Wi-Fi
One surefire way to give away your online banking password is to log in while on public Wi-Fi. Hackers hang out on public hot spots and spy on the activity of others. You should never type in a password or other sensitive details when connected to public Wi-Fi.
Tips for Improving Online Banking Security
Turn On Two-Factor Authentication
Enable two-factor authentication in your online banking account. This is also known as multi-factor authentication or two-step verification. According to Microsoft, it can block 99.9% of fraudulent account login attempts.
Click here to read more about multi-factor authentication and the benefits it provides. Contact Databranch today for assistance with implementing this highly effective security measure for your business.
Set Up Banking Alerts
Time is of the essence when an intruder breaches your account. The faster you can notify your bank of the breach, the better. You could reduce the impact on you by having your account locked down immediately.
Set up banking alerts through your online banking. These can include things like low-balance alerts and login alerts.
Install an Antivirus & DNS Filtering On Your PC
It’s important to have reliable antivirus software on your PC. Many people don’t think about protecting their personal devices in the same manor as their company devices. Yet, they shop online and bank via laptops almost daily.
It’s also good to use a DNS filter. This is a filter that protects you from going to dangerous phishing sites by blocking them.
In search of a good antivirus for your company devices? Contact Databranch today to discuss our full endpoint protection software that will protect your employees against viruses, malware, ransomware, phishing and other cyber-attacks.
Take Phishing Training Classes
Do you know how to identify phishing? Are you up on all the newest scams? You can make yourself less vulnerable by taking our Cybersecurity Awareness Training. Knowing how to spot phishing via text, email, and phone can help you avoid becoming the next victim.
Our Cybersecurity Training Courses for 2023 is available now! Contact Databranch today for more information on these courses or how you can enroll in our Breach Prevention Platform and Security Awareness Training with simulated phishing tests.
Get Help Protecting Your Business from Scams
There are some key digital solutions we can put in place to keep your business safer from online threats. Contact us today at at 716-373-4467 x115 or [email protected] to schedule a chat about online security.
Article used with permission from The Technology Press.
Read More
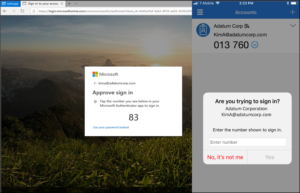
Upcoming Changes to Microsoft Office 365 Authenticator App
Microsoft has announced an upcoming change to the default method used in its Authenticator App. Starting May 8th, 2023, users will be required to input a verification number into the authenticator app. This date was previously February 27th, but Microsoft recently released a revision to the start date.
This number matching method is replacing the approve/deny push notification sent to mobile devices. Number matching is a key security upgrade to traditional second factor notifications in Microsoft Authenticator.
Microsoft will remove the admin controls and enforce the number match experience tenant-wide for all users starting May 8th, 2023.
Please note that this change will occur for both PCs and mobile devices. No action is required by the end users, this change will happen automatically by Microsoft.
If you have any questions regarding this upcoming change, or need any assistance, please contact Databranch Service at 716-373-4467 x4.
Microsoft Office 365 Changes to Security Defaults
Security Defaults are the preconfigured security settings that exist on your Microsoft accounts. Microsoft has announced that throughout the spring and summer of 2023, they will be rolling out Azure AD Security Defaults to all existing tenants.
Some of the changes enforced by the Security Defaults are below:
- Requiring all users and admins to register for MFA using the Microsoft Authenticator app.
- Challenging users with MFA, mostly when they show up on a new device or app, but more often for critical roles and tasks.
- Disabling authentication from legacy authentication clients that can’t do MFA.
- Protecting admins by requiring extra authentication every time they sign in.
Things to watch for:
- Automated emails/Reports from applications and vendors
- Scan to File Share
- Email functionality from applications
Customers will have the ability to disable the settings or configure alternate conditional access policies. However, disabling the Security Defaults would create vulnerabilities across your Microsoft accounts leaving your organization’s cybersecurity at risk.
Microsoft released Security Defaults back in 2019 to ensure that basic cybersecurity measures, such as MFA, were being used on their accounts. Because of this, over 30 million organizations already have baseline Security Defaults in place. This has allowed these companies to experience 80% less compromised accounts compared to companies without Security Defaults.
MFA alone is known for being the most effective tool at preventing compromised accounts, yet it is one of the most underutilized security measures. Microsoft’s Security Report states that MFA can block over 99.9% of account compromised attacks.
Databranch has taken the step of proactively enabling these Security Defaults for our own Microsoft tenant. This not only improves the cybersecurity of our Microsoft accounts, but it will also allow us to experience these changes first hand so we can better serve our clients.
We are also performing a review of the Office 365 tenants for all of our managed clients, so that we can proactively get their Security Defaults enabled, if they are not already.
Reach out today at [email protected] or 716-373-4467 if you have questions about these changes or wish to speak with one of our team members about enabling MFA for more accounts.
Read More

Misconfiguration of cloud solutions is often overlooked when companies plan cybersecurity strategies. Cloud apps are typically quick and easy to sign up for, so the user often assumes that they don’t need to worry about security because it’s handled.
This is an incorrect assumption because cloud security is a shared model. The provider of the solution handles securing the backend infrastructure but the user is responsible for configuring security settings in their account properly.
Problems with misconfiguration are the number one cause of cloud data breaches. It’s also an unforced error. Misconfiguration means that a company has made a mistake because it hasn’t adequately secured its cloud application.
Perhaps they gave too many employees administrative privileges or, they may have neglected to turn on a security function that would have prevented the downloading of cloud files by an unauthorized user.
Misconfiguration covers a wide range of negligent behavior. It all has to do with cloud security settings and practices. A finding in The State of Cloud Security 2021 shed light on how common this issue is. Around 45% of organizations experience between 1 and 50 cloud misconfigurations per day.
Some of the main causes of misconfiguration are:
- Lack of adequate oversight and controls
- A team lacking security awareness
- Too many cloud APIs to manage
- No adequate cloud environment monitoring
- Negligent insider behavior
- Not enough expertise in cloud security
Use the tips below to reduce your risk of a cloud data breach and improve cloud security.
Enable Visibility into Your Cloud Infrastructure
Do you know all the different cloud apps employees are using at your business? If not, you’re not alone. It’s estimated that shadow IT use is approximately 10x the size of known cloud use.
When an employee uses a cloud app without authorization, it’s considered “shadow IT.” This is because the app is in the shadows so to speak, outside the purview of the company’s IT team.
How can you protect something you don’t know about? This is why shadow cloud applications are so dangerous and why they often result in breaches due to misconfiguration.
Gain visibility into your entire cloud environment, so you know what you need to protect. One way you can do this is through a cloud access security application.
Restrict Privileged Accounts
The more privileged accounts you have, the higher the risk of a misconfiguration. There should be very few users that can change security configurations. You don’t want someone that doesn’t know better to accidentally open a vulnerability, such as removing a cloud storage sharing restriction. It could leave your entire environment a sitting duck for hackers.
Audit privileged accounts in all cloud tools. Then, reduce the number of administrative accounts to a least needed to operate.
Click here to learn more about the risks associated with Administrative Privileges.
Put in Place Automated Security Policies
Automation helps mitigate human error. Automating as many security policies as possible helps prevent cloud security breaches.
For example, if you use a feature like sensitivity labels in Microsoft 365, you can set a “do not copy” policy. It will follow the file through each supported cloud application. Users don’t need to do anything to enable it once you put the policy in place.
Use a Cloud Security Audit Tool (Like Microsoft Secure Score)
How secure is your cloud environment? How many misconfigurations might there be right now? It’s important to know this information so you can correct issues to reduce risk.
Use an auditing tool, like Microsoft Secure Score. You want a tool that can scan your cloud environment and let you know where problems exist. It should also be able to provide recommended remediation steps.
Set Up Alerts for When Configurations Change
Once you get your cloud security settings right, they won’t necessarily stay that way. Several things can cause a change in a security setting without you realizing it. These include:
- An employee with elevated permissions accidentally changes them
- A change caused by an integrated 3rd party plug-in
- Software updates
- A hacker that has compromised a privileged user credential
Be proactive by setting up alerts. You should have an alert for any significant change in your cloud environment. For example, when the setting to force multi-factor authentication gets turned off.
If an alert is set up, then your team knows right away when a change occurs to an important security setting. This allows them to take immediate steps to research and rectify the situation.
Have a Cloud Specialist Check Your Cloud Settings
Business owners, executives, and office managers usually are not cybersecurity experts and no one should expect them to know how to configure the best security for your organization’s needs.
It’s best to have a cloud security specialist from Databranch check your settings. Thinking about moving your applications from your local server to the cloud? We can help ensure that they’re set up to keep your data protected without restricting your team.
Improve Cloud Security & Lower Your Chances for a Data Breach
Most work is now done in the cloud, and companies store data in these online environments. Don’t leave your company at risk by neglecting to review your cloud security configuration. Contact Databranch today at 716-373-4467 x 115 or [email protected] to set up a cloud security assessment.
Article used with permission from The Technology Press.
Read More


















